Integrate OpenLDAP with Keycloak
This guide explains how to integrate OpenLDAP with Portworx Backup Keycloak for centralized user authentication and authorization. This integration allows you to use your existing LDAP directory for user management in Portworx Backup.
Prerequisites
Before you begin, ensure you have:
-
OpenLDAP server installed and configured
- Server accessible from the Portworx Backup cluster
- Administrative access to the LDAP server
- LDAP service running on standard ports (389 for LDAP, 636 for LDAPS)
-
LDAP directory structure with:
- Users organized in a specific organizational unit (OU)
- Groups organized in a specific organizational unit (OU)
- Proper LDAP schema for user and group objects
-
Portworx Backup installed and running with:
- Access to Keycloak admin console
- Administrative privileges in Keycloak
-
Network connectivity between Keycloak and LDAP server with:
- Firewall rules allowing LDAP traffic
- DNS resolution for LDAP server hostname (if using FQDN)
LDAP Directory Structure Example
For this integration, your LDAP directory should follow a structure similar to:
dc=example,dc=com
├── ou=users,dc=example,dc=com
│ ├── uid=john,ou=users,dc=example,dc=com
│ ├── uid=jane,ou=users,dc=example,dc=com
│ └── uid=admin,ou=users,dc=example,dc=com
└── ou=groups,dc=example,dc=com
├── cn=pxb-admins,ou=groups,dc=example,dc=com
├── cn=pxb-users,ou=groups,dc=example,dc=com
└── cn=pxb-operators,ou=groups,dc=example,dc=com
Configure LDAP User Federation
-
Navigate to the Keycloak admin console:
http://<NODE_IP>:<NODE_PORT>/auth/admin/For detailed instructions on accessing the Keycloak console, refer to Configure access to web console.
-
Log in with administrator credentials
-
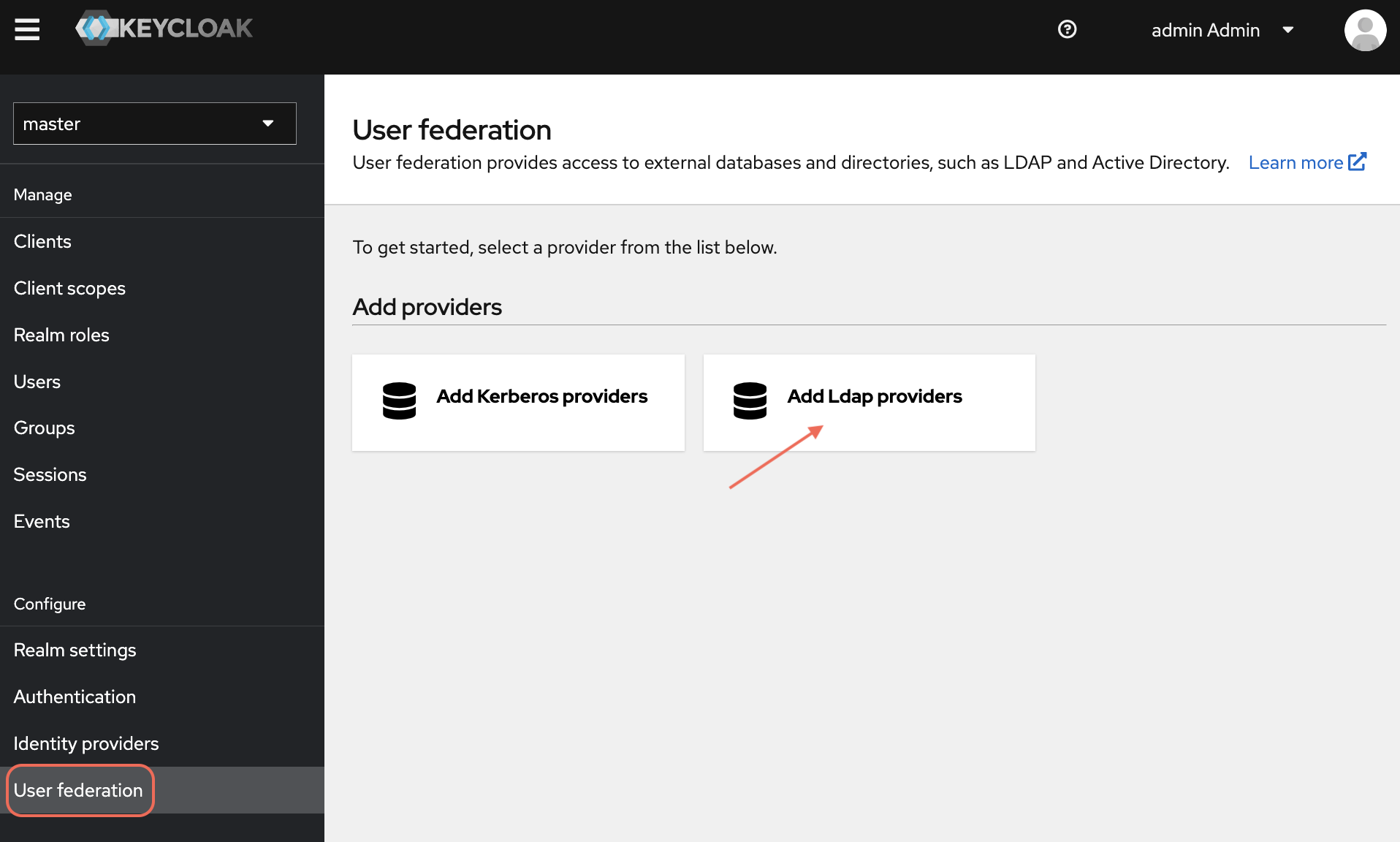
In the left navigation pane, click User Federation.
-
Click Add provider and select ldap:
-
In the Add user federation provider page, configure the following:
General Options
- Console Display Name:
OpenLDAP - Vendor: Select
Otherfrom the dropdown - Priority:
0(default priority)
Connection Settings
- Connection URL:
ldap://<LDAP_SERVER_IP>:389- For secure connections:
ldaps://<LDAP_SERVER_IP>:636 - Example:
ldap://192.168.1.100:389
- For secure connections:
- Enable StartTLS:
OFF(unless using StartTLS) - Use Truststore SPI:
Only for ldaps(for LDAPS connections) - Connection Pooling:
ON(recommended for performance) - Connection Timeout:
5000(milliseconds)
- Console Display Name:
-
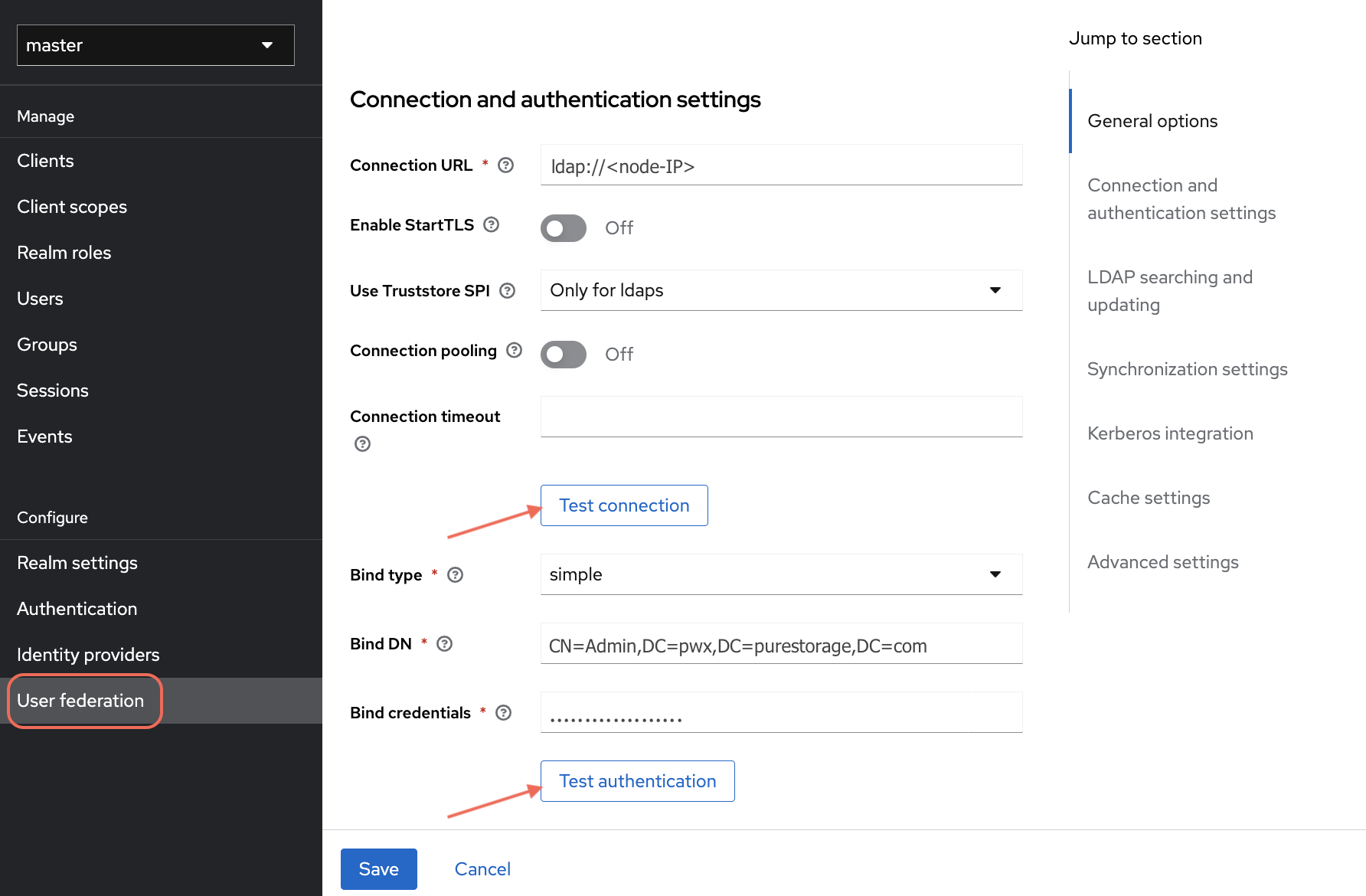
Click Test connection to verify the connection settings
Authentication Settings
- Bind Type:
simple - Bind DN:
cn=admin,dc=example,dc=com- Replace with your LDAP admin user DN
- Bind Credential: Enter the password for the bind DN user
- Bind Type:
-
Click Test authentication to verify the bind credentials
-
Configure the following search and update settings:
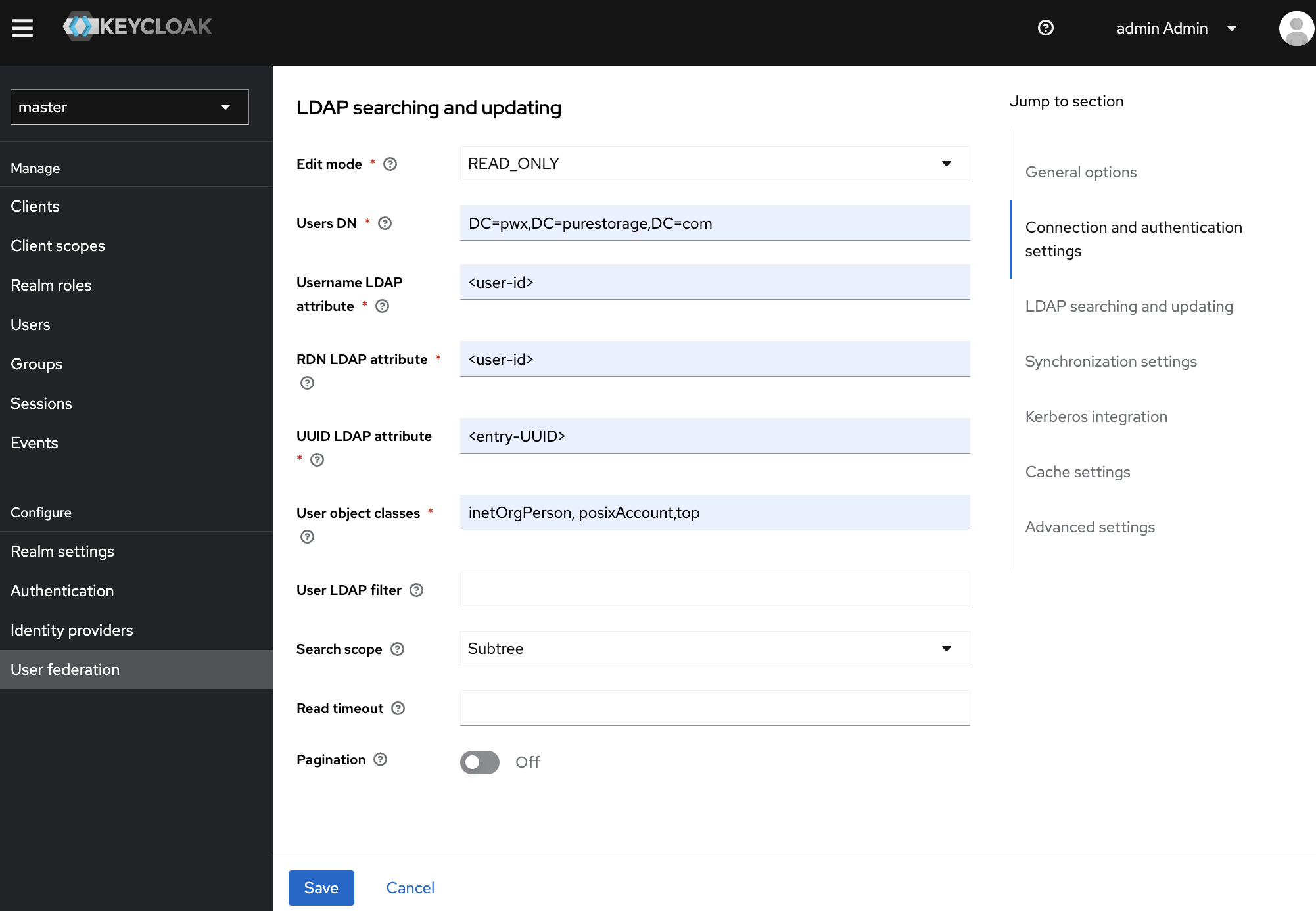
LDAP Searching and Updating
-
Edit Mode:
READ_ONLY(recommended for production) -
Users DN:
ou=users,dc=example,dc=com- The DN where user entries are located
-
Username LDAP Attribute:
uid- Attribute used for username (common:
uid,cn,sAMAccountName)
- Attribute used for username (common:
-
RDN LDAP Attribute:
uid- Relative Distinguished Name attribute
-
UUID LDAP Attribute:
entryUUID- For OpenLDAP, use
entryUUID; for Active Directory, useobjectGUID
- For OpenLDAP, use
-
User Object Classes:
inetOrgPerson,organizationalPerson,person- Object classes for user entries
-
User LDAP Filter:
(objectClass=inetOrgPerson)- Optional filter to limit user search
-
Search Scope:
One Level- Search only direct children of Users DN
-
Read Timeout:
10000(milliseconds) -
Pagination:
ON(recommended for large directories)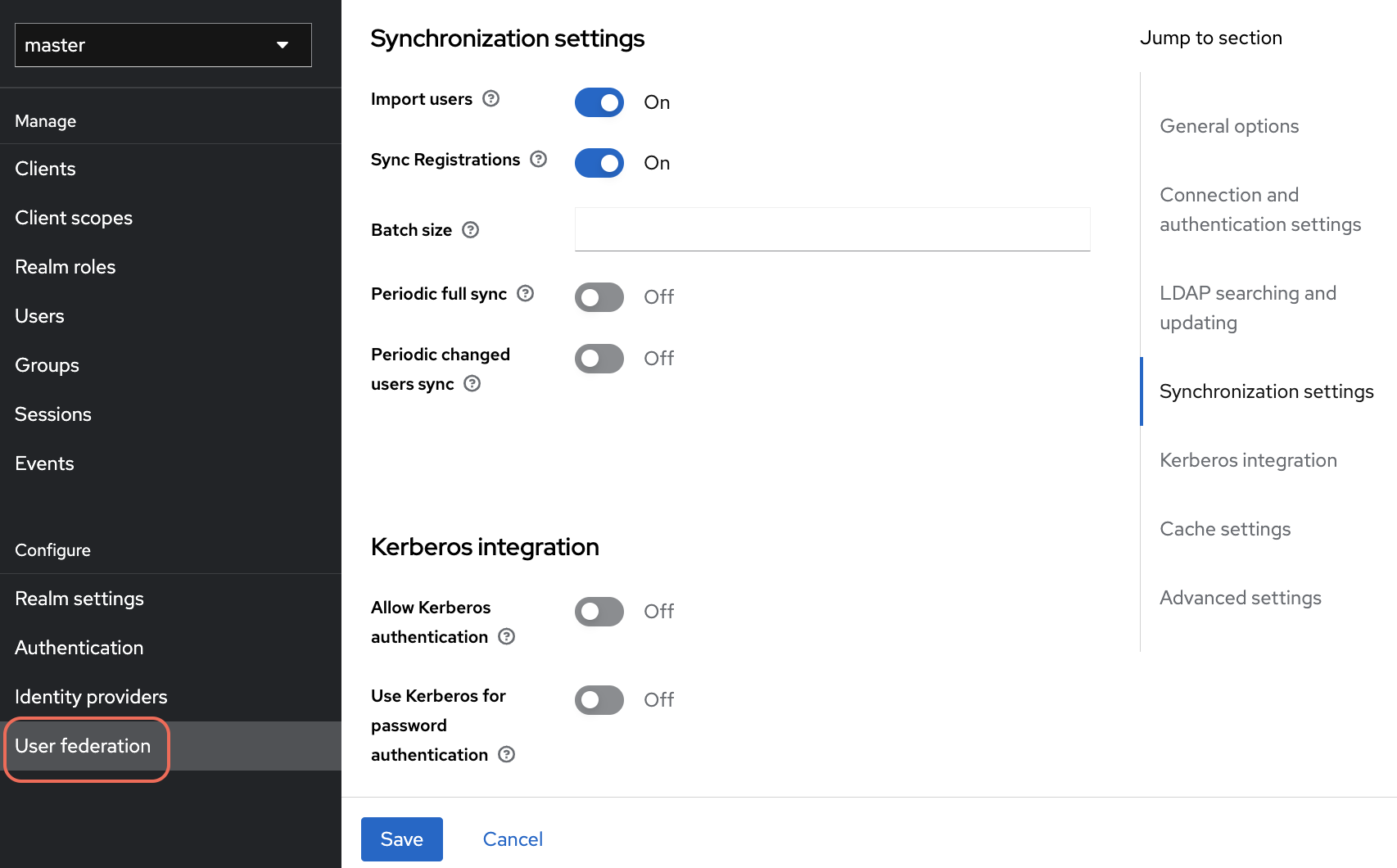
Synchronization Settings
- Import Users:
ON- Import existing LDAP users into Keycloak
- Sync Registrations:
OFF- Disable if you don't want new Keycloak users created in LDAP
- Batch Size:
1000- Number of users to sync in each batch
- Periodic Full Sync:
ON(optional)- Full Sync Period:
604800(7 days in seconds)
- Full Sync Period:
- Periodic Changed Users Sync:
ON(optional)- Changed Users Sync Period:
86400(24 hours in seconds)
- Changed Users Sync Period:
Kerberos Integration
- Allow Kerberos Authentication:
OFF - Use Kerberos for Password Authentication:
OFF
Cache Settings
- Cache Policy:
DEFAULT - Eviction Day: Leave empty
- Eviction Hour: Leave empty
- Eviction Minute: Leave empty
- Max Lifespan:
3600000(1 hour in milliseconds)
Advanced Settings
- Enable the LDAPv3 Password Modify Extended Operation:
OFF - Validate Password Policy:
OFF - Trust Email:
ON- Enable if LDAP email addresses are trusted
-
-
Click Test connection to verify connectivity
-
Click Test authentication to verify bind credentials
-
Click Save to create the LDAP provider
Your OpenLDAP server is now integrated with Keycloak. Users can npw login to Portworx Backup web console using their OpenLDAP credentials.
Configure Group Mappers
After creating the LDAP provider, configure mappers to synchronize groups and user attributes.
-
Navigate to User Federation in the left navigation pane.
-
Select your OpenLDAP provider.
-
Click the Mappers tab.
-
Click Add Mapper to add a new mapper.
-
Configure the following settings:
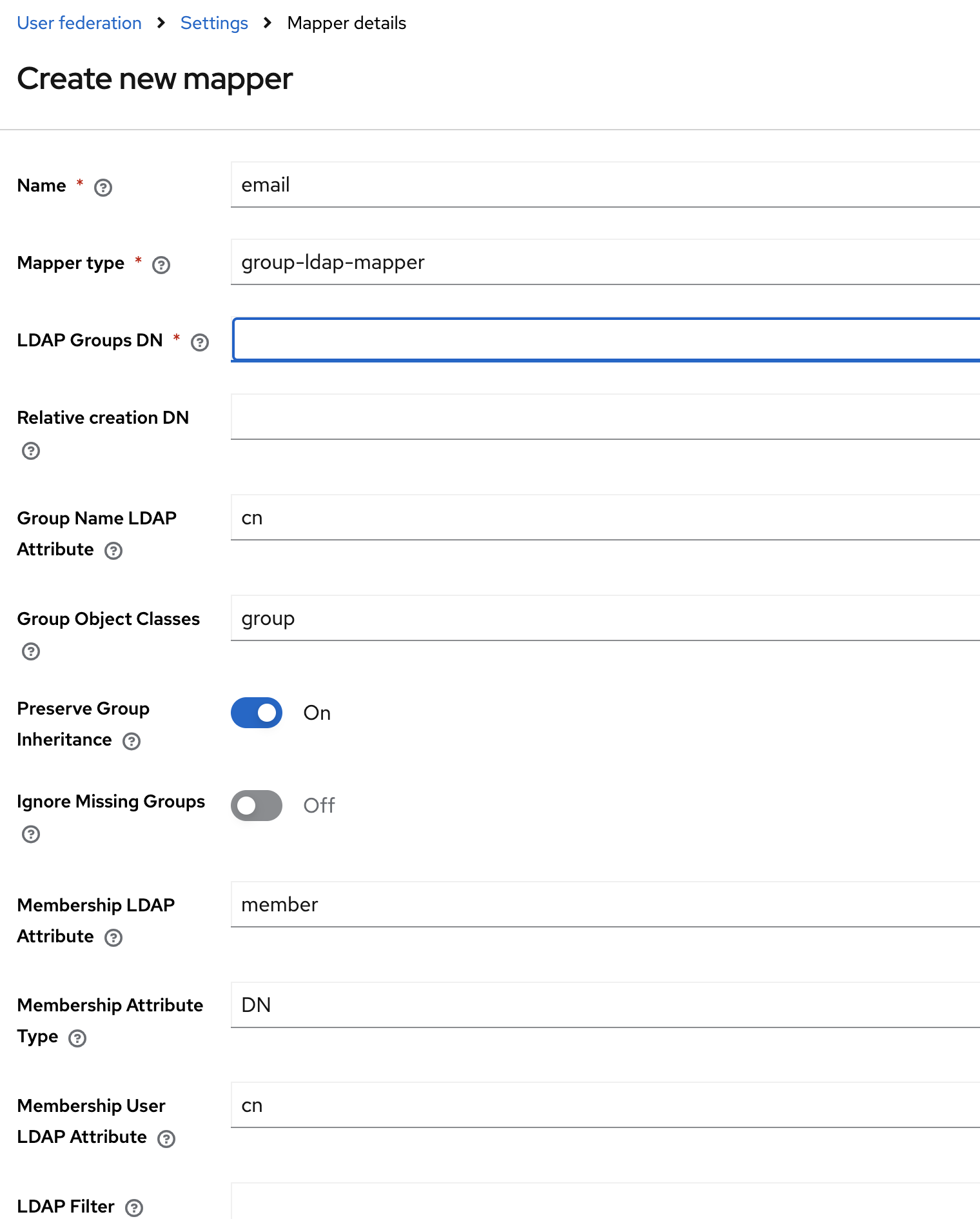
Basic Settings
- Name:
ldap-group-mapper - Mapper Type:
group-ldap-mapper
Group Settings
- LDAP Groups DN:
ou=groups,dc=example,dc=com- The DN where group entries are located
- Group Name LDAP Attribute:
cn- Attribute used for group name
- Group Object Classes:
groupOfNames,top- Object classes for group entries
- Preserve Group Inheritance:
OFF- Set to ON if you have nested groups
- Ignore Missing Groups:
OFF - Membership LDAP Attribute:
member- Attribute that contains group members
- Membership Attribute Type:
DN- How members are referenced (DN or UID)
- Membership User LDAP Attribute:
uid- User attribute for membership mapping
- LDAP Filter:
(objectClass=groupOfNames)- Optional filter for group search
- Mode:
READ_ONLY - User Groups Retrieve Strategy:
LOAD_GROUPS_BY_MEMBER_ATTRIBUTE
- Name:
-
Click Save to create the group mapper.
-
In the Mappers tab, under Actions select the required sync option to sync the users and groups.
-
Verify that groups are imported successfully.
-
You can create additional mappers for user attributes:
Email Mapper
- Name:
email - Mapper Type:
user-attribute-ldap-mapper - User Model Attribute:
email - LDAP Attribute:
mail - Read Only:
ON
First Name Mapper
- Name:
first name - Mapper Type:
user-attribute-ldap-mapper - User Model Attribute:
firstName - LDAP Attribute:
givenName - Read Only:
ON
Last Name Mapper
- Name:
last name - Mapper Type:
user-attribute-ldap-mapper - User Model Attribute:
lastName - LDAP Attribute:
sn - Read Only:
ON
- Name:
Troubleshooting
Connection Problems
- Verify LDAP server is accessible from Keycloak
- Check firewall rules and network connectivity
- Ensure correct LDAP server URL and port
Authentication Failures
- Verify bind DN and credentials are correct
- Check LDAP server logs for authentication errors
- Ensure bind user has sufficient privileges
User/Group Sync Issues
- Verify Users DN and Groups DN are correct
- Check LDAP filters and object classes
- Review LDAP directory structure and permissions
Performance Issues
- Enable connection pooling
- Adjust batch size for synchronization
- Consider using pagination for large directories
Log Analysis
Check Keycloak server logs for detailed error messages.
Next Steps
After successfully integrating OpenLDAP with Keycloak:
- Configure Role Mappings: Map LDAP groups to Portworx Backup roles
- Set Up Rancher Integration: If using Rancher, configure RBAC integration
- Test User Access: Verify users can access Portworx Backup with appropriate permissions
- Monitor Synchronization: Set up periodic sync to keep users and groups updated