Install on Air-gapped Environments
This topic explains how you can prepare your clusters in an air-gapped environment and install Portworx Backup on-premises.
For installation through Argo CD, refer to Argo CD installation topic.
Prepare air-gapped environments
If your cluster is internet-connected, skip this section. If your cluster is air-gapped, you must pull the below Docker images to either your docker registry or your server. If you are using your own Prometheus and Alertmanager with Portworx Backup, you do not have to pull the last four images from the following list:
- 2.9.1
- 2.9.0
| Image | Image path | Version |
|---|---|---|
| pxcentralOnpremApi | docker.io/portworx/pxcentral-onprem-api | 2.9.1 |
| pxcentralOnpremUiFrontend | docker.io/portworx/pxcentral-onprem-ui-frontend | 2.9.1 |
| pxcentralOnpremUiBackend | docker.io/portworx/pxcentral-onprem-ui-backend | 2.9.1 |
| pxcentralOnpremUiLhbackend | docker.io/portworx/pxcentral-onprem-ui-lhbackend | 2.9.1 |
| pxcentralOnpremPreSetup | docker.io/portworx/pxcentral-onprem-hook | 2.9.1 |
| pxcentralOnpremPostSetup | docker.io/portworx/pxcentral-onprem-post-setup | 2.9.1 |
| pxBackup | docker.io/portworx/px-backup | 2.9.1 |
| postgresql | docker.io/portworx/postgresql | 17.4.0-debian-12-r19 |
| keycloak | docker.io/portworx/keycloak | 26.2.4 |
| keycloakLoginTheme | docker.io/portworx/keycloak-login-theme | 2.9.1 |
| busybox | docker.io/portworx/busybox | 1.35.0 |
| mysql | docker.io/portworx/mysql | 8.0.40 |
| mongodb | docker.io/portworx/mongodb | 8.0.9-debian-12-r1 |
| mongodb7 | docker.io/portworx/mongodb | 7.0.15-debian-12-r2 |
| mongodb6 | docker.io/portworx/mongodb | 6.0.13-debian-11-r21 |
| mongodb5 | docker.io/portworx/mongodb | 5.0.24-debian-11-r20 |
| kopiaExecutor | docker.io/portworx/kopiaexecutor | 1.2.20 |
| nfsExecutor | docker.io/portworx/nfsexecutor | 1.2.20 |
| filesystemCtl | docker.io/portworx/filesystemctl | 1.2.20 |
| pxBackupPrometheusImage | docker.io/portworx/prometheus | v3.3.1 |
| pxBackupAlertmanagerImage | docker.io/portworx/alertmanager | v0.28.0 |
| pxBackupPrometheusOperatorImage | docker.io/portworx/prometheus-operator | v0.82.1 |
| pxBackupPrometheusConfigReloaderImage | docker.io/portworx/prometheus-config-reloader | v0.82.1 |
| pxLicenseServer | docker.io/portworx/px-els | 2.8.0 |
| Image | Image path | Version |
|---|---|---|
| pxcentralOnpremApi | docker.io/portworx/pxcentral-onprem-api | 2.9.0 |
| pxcentralOnpremUiFrontend | docker.io/portworx/pxcentral-onprem-ui-frontend | 2.9.0 |
| pxcentralOnpremUiBackend | docker.io/portworx/pxcentral-onprem-ui-backend | 2.9.0 |
| pxcentralOnpremUiLhbackend | docker.io/portworx/pxcentral-onprem-ui-lhbackend | 2.9.0 |
| pxcentralOnpremPreSetup | docker.io/portworx/pxcentral-onprem-hook | 2.9.0 |
| pxcentralOnpremPostSetup | docker.io/portworx/pxcentral-onprem-post-setup | 2.9.0 |
| pxBackup | docker.io/portworx/px-backup | 2.9.0 |
| postgresql | docker.io/portworx/postgresql | 17.4.0-debian-12-r19 |
| keycloak | docker.io/portworx/keycloak | 26.2.4 |
| keycloakLoginTheme | docker.io/portworx/keycloak-login-theme | 2.9.0 |
| busybox | docker.io/portworx/busybox | 1.35.0 |
| mysql | docker.io/portworx/mysql | 8.0.40 |
| mongodb | docker.io/portworx/mongodb | 8.0.9-debian-12-r1 |
| mongodb7 | docker.io/portworx/mongodb | 7.0.15-debian-12-r2 |
| mongodb6 | docker.io/portworx/mongodb | 6.0.13-debian-11-r21 |
| mongodb5 | docker.io/portworx/mongodb | 5.0.24-debian-11-r20 |
| kopiaExecutor | docker.io/portworx/kopiaexecutor | 1.2.19 |
| nfsExecutor | docker.io/portworx/nfsexecutor | 1.2.19 |
| filesystemCtl | docker.io/portworx/filesystemctl | 1.2.19 |
| pxBackupPrometheusImage | docker.io/portworx/prometheus | v3.3.1 |
| pxBackupAlertmanagerImage | docker.io/portworx/alertmanager | v0.28.0 |
| pxBackupPrometheusOperatorImage | docker.io/portworx/prometheus-operator | v0.82.1 |
| pxBackupPrometheusConfigReloaderImage | docker.io/portworx/prometheus-config-reloader | v0.82.1 |
| pxLicenseServer | docker.io/portworx/px-els | 2.8.0 |
| Stork | openstorage/stork | 25.3.1 |
| Command Executor | openstorage/cmdexecutor | 25.3.1 |
| NFS Executor | openstorage/nfsexecutor | 1.2.19 |
| Kopia Executor | openstorage/kopiaexecutor | 1.2.19 |
- Refer to the Install Stork in air-gapped environments section to know more about the Stork and other
openstorageimages in your air-gapped environment, before installing Portworx Backup. - If your application cluster is running in the IBM Cloud environment, ensure that the image repository path is set to
icr.io/ext/portworx/stork:<supported-pxb-stork-version>before applying thestork-spec.yamlduring Stork installation (without PXE).
To pull the above Docker images and push them to an internal registry:
-
Download the
pxcentral-ag-install-backup.shair-gapped bootstrap Portworx Backup install script.curl -o pxcentral-ag-install-backup.sh -L "https://install.portworx.com/pxcentral-air-gapped?px-backup=true"You can also download the install script for a specific release by specifying a
versionquery. For example:curl -o pxcentral-ag-install-backup.sh -L "https://install.portworx.com/pxcentral-air-gapped?version=2.9.1&px-backup=true"
-
Provide execute permission for the install script:
chmod +x pxcentral-ag-install-backup.sh -
Pull the container images to your local setup using the
pxcentral-ag-install-backup.shscript:./pxcentral-ag-install-backup.sh pull -
Push the images to a internal registry server, accessible by the air-gapped nodes. Replace
<repo>with your registry location../pxcentral-ag-install-backup.sh push <repo> -
Access Portworx Central specgen.
-
From the home page, navigate to Backup Services under Explore our Products.
-
Click on I agree to EULA and go through the Portworx Products Terms of Use carefully.
-
Navigate back to the Portworx Central portal and click Start Free Trial.
-
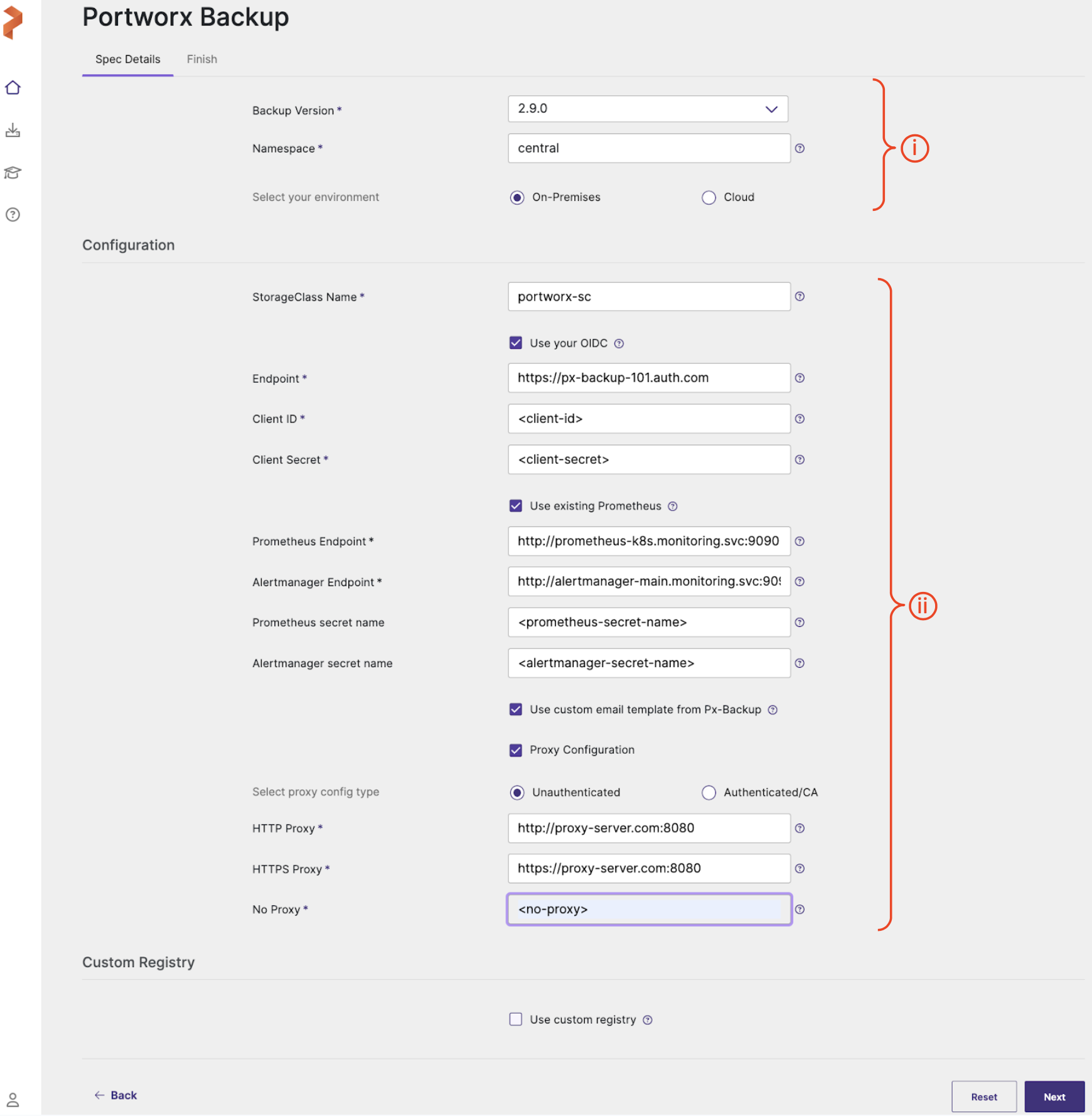
In the Spec Details provide the following values:
- Release Information
-
Backup Version: select the required version of Portworx Backup from the drop-down list
-
Namespace: provide the name of the namespace where you want an instance of Portworx Backup to be installed
-
Select your environment: choose On-Premises or Cloud based on your storage environment
- Configuration
-
StorageClass Name: name of the StorageClass, refer tooltip for more details
-
Use your OIDC: select this checkbox only if your external authorization provider is Auth0 and key in the following fields:
- Endpoint
- Client ID
- Client Secret
These values can be fetched from the Auth0 web console. For more information on integrating external authorization providers, refer to Integrate Auth Providers
-
Use existing Prometheus: select this checkbox if you have to use your existing Prometheus stack to monitor Portworx Backup and enter the values for the following fields:
- Prometheus Endpoint: enter details of the endpoint where your Prometheus is installed
- Alertmanager Endpoint: enter details of the endpoint where your Alertmanager is installed
- Prometheus secret name: enter secret name of your Prometheus stack
- Alertmanager secret name: enter secret name of your Alertmanager
- Use Custom email template from PX-Backup: select to upload Portworx Backup's custom email template to your pre-configured Alertmanager for email notifications
-
Proxy Configuration: select this checkbox if you have proxy server configured in your environment and enter the values for the following fields:
- Unathenticated: choose this if you have unathenticated proxy server
- HTTP Proxy: proxy server URL for http proxy
- HTTPS Proxy: proxy server URL for https proxy
- NO PROXY: comma separated list of hostnames IPs or domains that should bypass the proxy settings
- Authenticated/CA: choose this option if your cluster is behind a proxy server with authentication or CA
- Proxy configuration secret: name of the kubernetes proxy configuration secret created in pxb namespace holding the proxy configuration
- Unathenticated: choose this if you have unathenticated proxy server
-
Use custom registry: for air-gapped environments
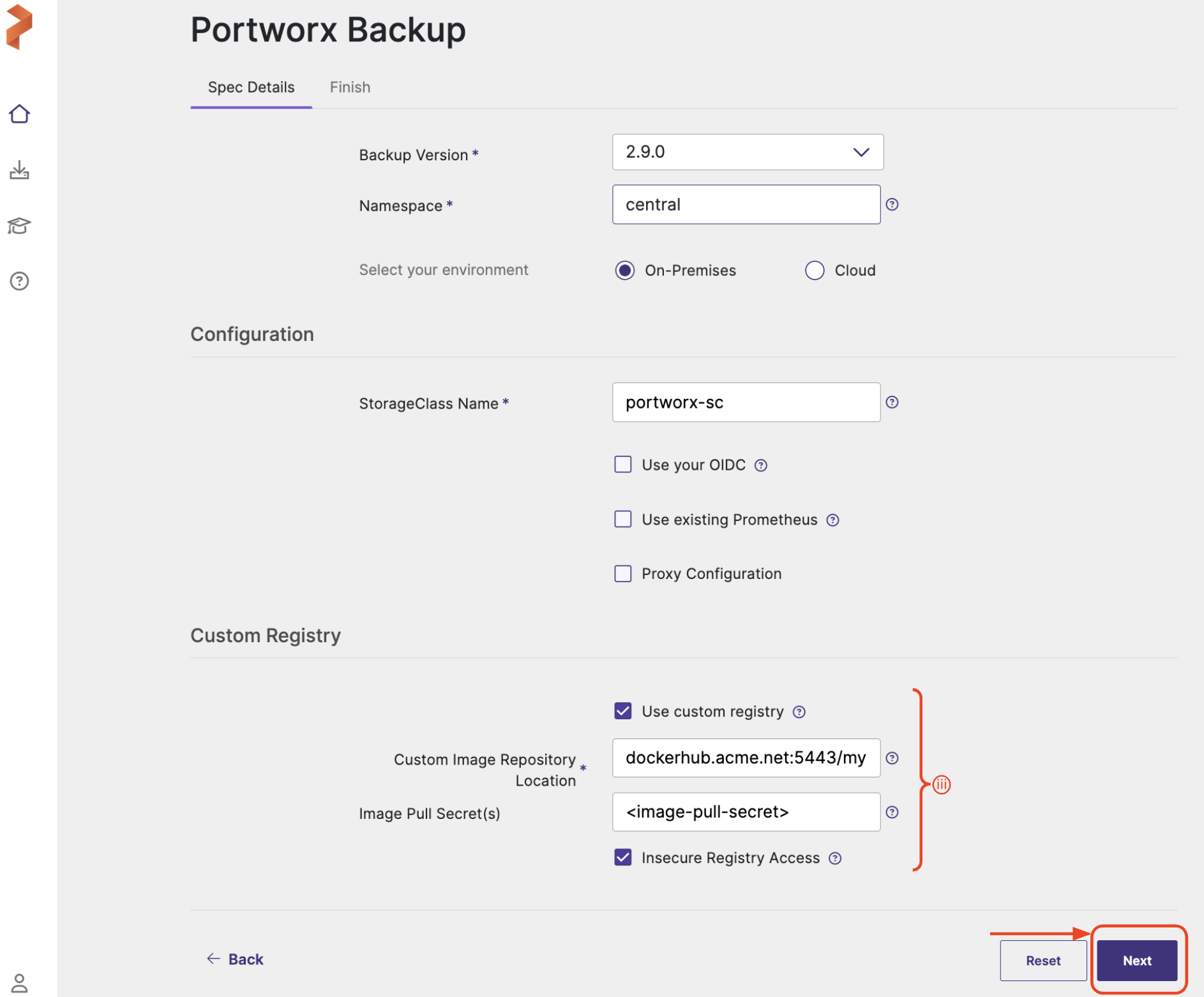
- Custom Image Repository Location: path of custom image repository
- Image Pull Secret(s): create a secret in the following cases:
- If image pulling from an internal repository requires credentials
- If you were using
docregistry-secret
-
Click Next to navigate to Finish tab.
-
In the Finish tab:
-
Step 1:
-
Execute the below command to add and then update helm repo:
helm repo add portworx http://charts.portworx.io/ && helm repo update
-
-
Step 2:
- Click
values-px-central.yamlfile to download the default options.
- Click
-
-
From the instance where you run the
helm3command:-
Download the latest
px-centralpackage with the following command:curl -O https://raw.githubusercontent.com/portworx/helm/master/stable/px-central-2.9.1.tgz -
Modify the Helm command generated from second option of Step 2 (of Portworx Backup web console) to provide the helm package, instead of providing the repository. For example:
helm install px-central portworx/px-central --namespace <pxb-namespace> --create-namespace --version 2.9.1 -f values-px-central.yaml
Following is the modified command for air-gapped environment using the downloaded helm package:
helm install px-central px-central-.tgz --namespace <pxb-namespace> --create-namespace --version 2.9.1 -f values-px-central.yaml
- Click Finish after you complete the installation through CLI way. You can find more information about the Portworx Backup Helm chart in the helm section.
-