Upgrade PXB on Non Air-Gapped Environments
Portworx Backup supports upgrades to version n from versions n-1 or n-2 versions. For example, if you are on Portworx Backup version 2.8.x, you can directly upgrade to 2.10.2. If you are on 2.6.x and want to upgrade to 2.10.2, you need to upgrade in phased manner. First upgrade from version 2.6.x to 2.8.x, and then upgrade from version 2.8.x to 2.10.2.
Refer the Argo CD install topic for install/upgrade PXB through Argo CD.
Upgrade Portworx Backup in non-airgapped Environment
To upgrade to required version of Portworx Backup:
- Spec Details
- Finish
-
Access Portworx Central portal.
-
Enter login credentials and make sure that you go through End-User License Agreement (EULA).
If you are new to Portworx Central, click on Create account to generate your login credentials. You can also sign in with your organization’s OIDC identity provider, Google or Github account.
-
Click Sign In to access the Portworx Central portal.
-
On the home page, under Explore our Products, navigate to the Portworx Backup card. Then click Generate Backup Spec to open the Portworx Backup Install/upgrade page (Spec Details tab).
-
In the Spec Details tab provide the following values:
-
Backup Version: select the required version of Portworx Backup from the drop-down, here it is 2.10.2
-
Namespace: provide the name of the namespace where you want an instance of Portworx Backup to be installed
-
Select your environment: choose On-Premises or Cloud based on your storage environment
-
StorageClass Name: name of the StorageClass, refer tooltip for more details

- Release data:
-
Backup Version: select the required version of Portworx Backup from the drop-down
-
Namespace: provide the name of the namespace where you want an instance of Portworx Backup to be installed
-
Select your environment: choose On-Premises or Cloud based on your storage environment
-
Configuration
- StorageClass Name: name of the StorageClass, refer tooltip for more details
noteDefining the namespace and StorageClass is a one-time configuration step that should be completed during the initial installation. PVCs will be created using Namespace and StorageClass values you define in the SpecGen, and these values cannot be modified later during an upgrade.
-
Enable Rancher RBAC: select this checkbox if you are using Rancher for managing your Kubernetes clusters and want to enable Rancher's Role-Based Access Control (RBAC) for Portworx Backup. This feature can be enabled only if you have LDAP or PingIdentity as your identity provider. For more information, refer to Rancher RBAC Integration with Namespace Filtering and Rancher RBAC.
-
Use your OIDC: select this option only if your external authorization provider is Auth0 and key in the following fields:
- Endpoint
- Client ID
- Client Secret
These values can be fetched from the Auth0 web console.
-
Use existing Prometheus: select this checkbox if you have to use your existing Prometheus stack to monitor Portworx Backup and enter the values for the following fields:
-
Prometheus Endpoint: enter details of the endpoint where your Prometheus is installed
-
Alertmanager Endpoint: enter details of the endpoint where your Alertmanager is installed
-
Prometheus secret name: enter secret name of your Prometheus stack
-
Alertmanager secret name: enter secret name of your Alertmanager
-
Custom email template from PX-Backup: select to upload Portworx Backup's custom email template to your pre-configured Alertmanager for email notifications
By default, persistent volume size for Prometheus server is 5 GB, if you need more storage, use the following command during the upgrade from previous versions of Portworx Backup to 2.10.2:
--set persistentStorage.prometheus.storage=8Gi, persistentStorage.prometheus.retentionSize=<92% of prometheus.storage in MB>7360MBThe command above resets the Prometheus server's persistent volume size to 8 GB. You can set the required storage based on your needs.
-
-
Proxy Configuration: select this checkbox if you have proxy server configured in your environment and enter the values for the following fields:
- Unathenticated: choose this if you have unathenticated proxy server
- HTTP Proxy: proxy server URL for http proxy
- HTTPS Proxy: proxy server URL for https proxy
- NO PROXY: Comma separated list of hostnames IPs or domains that should bypass the proxy settings
- Authenticated/CA: choose this option if your cluster is behind a proxy server with authentication or CA
-
Proxy configuration secret: name of the kubernetes proxy configuration secret created in pxb namespace holding the proxy configuration
-
- Unathenticated: choose this if you have unathenticated proxy server
-
Custom Registry
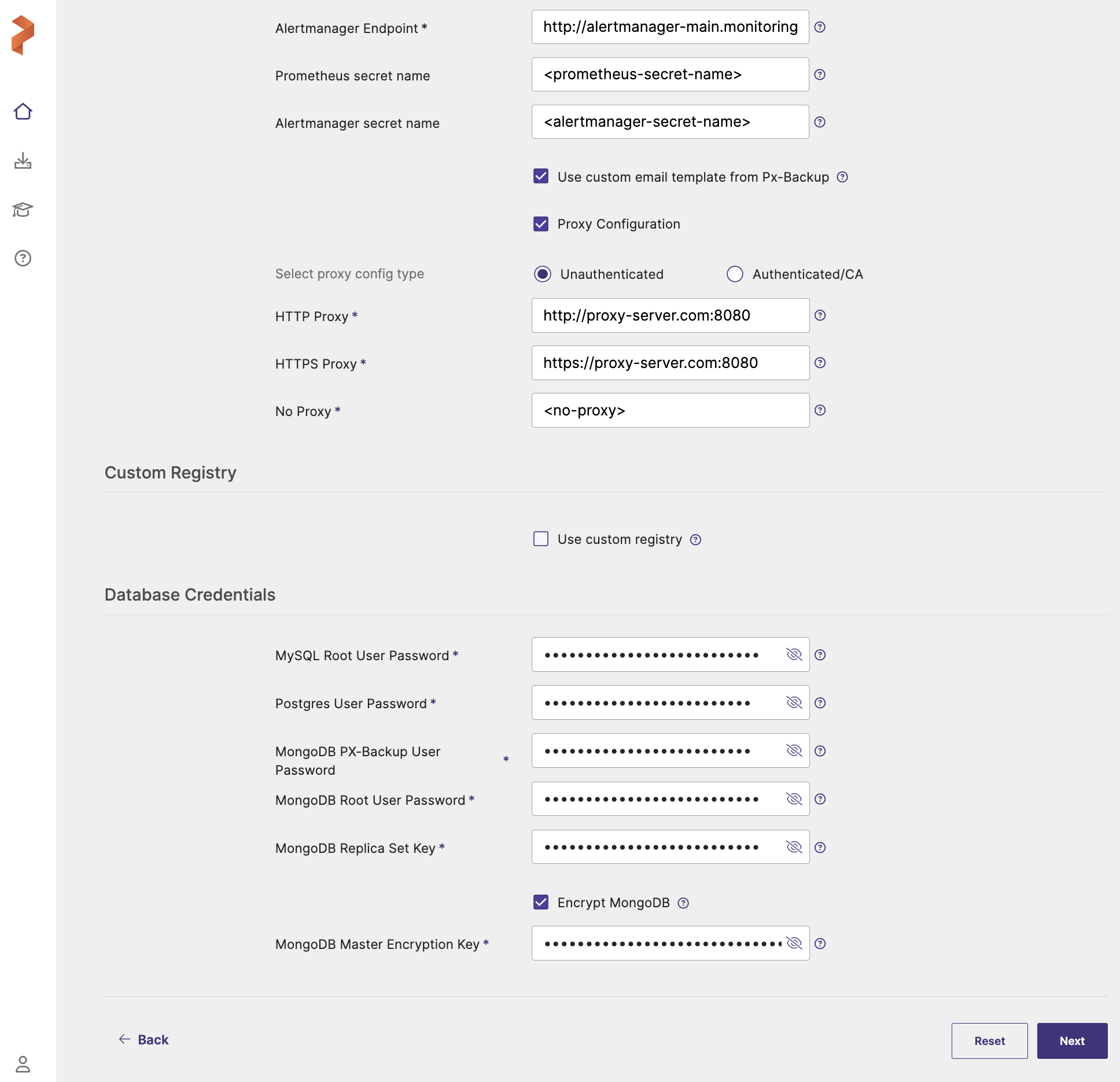
- Use custom registry: applicable only for air-gapped environments, do not select this check-box for non-airgapped system.
-
Database Credentials: This section configures database passwords for the various database components used by Portworx Backup. For guidelines on how to set the database credentials, refer to Password Policy.
-
MySQL Root User Password: root password for MySQL database
-
Postgres User Password: password for PostgreSQL user
-
MongoDB PX-Backup User Password: password for MongoDB PX-Backup user
-
MongoDB Root User Password: root password for MongoDB database
-
MongoDB Replica Set Key: key for MongoDB replica set authentication
-
Encrypt MongoDB: select this checkbox to enable encryption at rest for MongoDB database
-
MongoDB Master Encryption Key: Master encryption key for MongoDB encryption at rest
cautionSafeguarding your encryption key is vital to prevent permanent data loss. If the key is lost, you will be unable to access your encrypted data, as it is the only means of decryption. Without it, the data is rendered completely inaccessible and cannot be recovered. Note that encryption keys cannot be rotated after they are set.
-
-
-
Click Next to navigate to Finish tab.
Navigate to the Finish tab at the top to execute few commands to complete the installation.
Finish Tab
Finish tab provides you with the generated Kubernetes manifests and Helm commands needed to complete the installation of Portworx Backup in your environment.
- In the Finish tab:
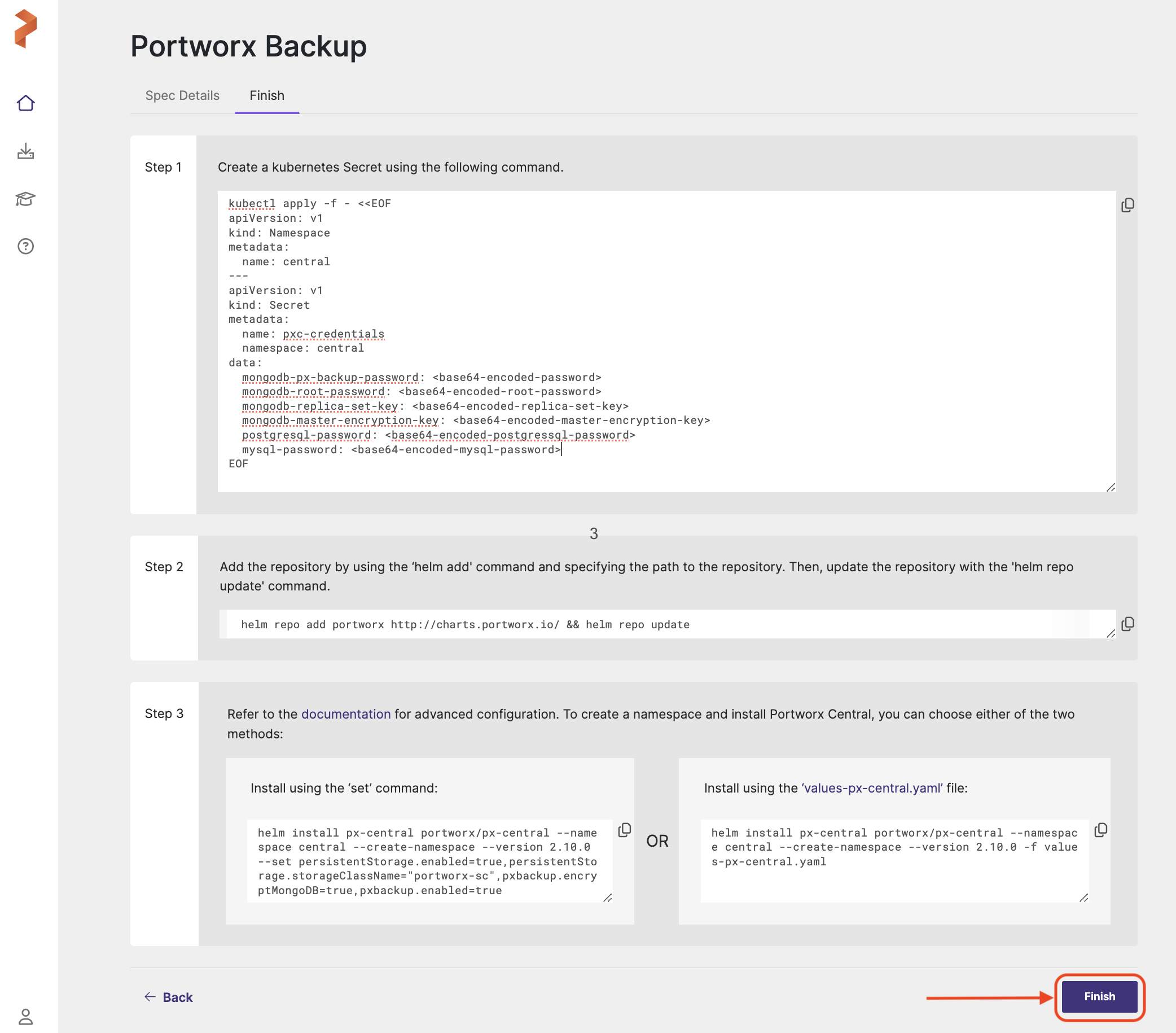
Step 1
-
Copy the below yaml (command under Step 1) to your terminal and run tocreate a Kubernetes secret containing database credentials and configuration parameters for Portworx Backup components.
pxc-credentials secretkubectl apply -f - <<EOF
apiVersion: v1
kind: Namespace
metadata:
name: <pxb-namespace>
---
apiVersion: v1
kind: Secret
metadata:
name: pxc-credentials
namespace: <pxb-namespace>
data:
mongodb-px-backup-password: <base64-encoded-mongodb-password>
mongodb-root-password: <base64-encoded-mongodb-root-password>
mongodb-replica-set-key: <base64-encoded-mongodb-replica-set-key>
mongodb-master-encryption-key: <base64-encoded-mongodb-master-encryption-key>
postgresql-password: <base64-encoded-postgresql-password>
mysql-password: <base64-encoded-mysql-password>
EOFThe command creates the specified namespace (for example, central) and generates a
pxc-credentialssecret containing database passwords. All sensitive data is automatically base64-encoded for security, and the database credentials include password, replica set, and encryption key for MongoDB, only passwords for PostgreSQL and MySQL components of Portworx Backup.If
pxc-credentialssecret is not set, installing or upgrading Portworx Backup will fail with the following error:time="<UTC Timestamp>" level=fatal msg="Pre-install Hook failed: RunPreInstall: failed to validate custom passwords: ValidateCustomPasswordSecret: error validating pxc-credentials secret: secret pxc-credentials not found in namespace central"
Step 2
-
Execute the following command to add the helm repository to your cluster and update it:
helm repo add portworx http://charts.portworx.io/ && helm repo update
Step 3
You can upgrade Portworx Backup either with default options or with advanced options based on your environment. To upgrade Portworx Backup with default options, go with Install using set command. For upgrade with advanced options, go with Install using the values-px-central.yaml file.
To upgrade Portworx Backup with default or basic options:
-
Optional If you are deploying PXB in a cluster with Istio or linkerd as service mesh, append
istio.enabled=trueorlinkerd.enabled=trueat the end of the command provided under Install using thesetcommand.noteYou do not have to append
istio.enabled=trueif you have installed Istio in ambient mode.Sample command:
helm upgrade px-central charts/px-central --namespace central --version 2.10.0 --set persistentStorage.enabled=true,persistentStorage.storageClassName=”<storage-class-name>”,pxbackup.enabled=true,istio.enabled=trueNote that all the parameters you have provided in the Spec Details tab get appended after
--setin the command. -
After you are done with providing and appending all the required parameters for upgrade, verify the command for accuracy.
-
Now copy and run the command in the terminal to upgrade Portworx Backup.
OR
Option 2: Install using the values-px-central.yaml fileTo upgrade Portworx Backup with advanced options:
-
Click
values-px-central.yamlfile option provided under Install using the values-px-central.yaml file on the right of Step 2. This creates and downloads a values file namedvalues-px-central.yamlwith all your configuration overrides. -
Rename this as
values-px-central-<pxb-release-version>.yaml. Where<pxb-release-version>is the PXB version you want to install. -
Set the values for the below keys as
truebased on the service mesh you have deployed in PXB cluster. Note that by default,istio.enabledandlinkerd.enabledare set tofalse.hostNameis mandatory only if multiple application uses the same prefix "/":istio:
enabled: true
hostName: ""
linkerd:
enabled: true -
Save the yaml file for the changes made and validate the values.
-
From your CLI terminal, retrieve all custom values you used during the previous Portworx Backup installation or upgrade. These custom values are required for upgrade to retain the current configuration. Execute the following command to generate the current values YAML file:
helm get values --namespace <pxb-namespace> px-central -o yaml > values-current.yamlWhere
<pxb-namespace>is the namespace in which you are planning to upgrade PXB to the required latest version.The above command retrieves the values used to configure the
px-centralHelm release with helm get values, scoped to the specified namespace (--namespace <pxb-namespace>, such aspx-backup), and outputs them in YAML format (-o yaml). The results are then redirected into a file calledvalues-current.yaml, allowing you to review, back up, or modify the configuration for future use, such as during an upgrade. -
Compare the files you obtained from Step ii and Step v, and update the new
values-px-central-<pxb-release-version>.yamlif required to carry all the customizations you have made in the previous release.When you initially installed Portworx Backup using Helm, you likely customized several settings (for example, image registry paths, versions, storage class names, proxy configs, and so on). During an upgrade, you must retain these customizations to avoid overwriting your working setup. Helm upgrades are declarative, and if you do not pass your previous configuration again, Helm assumes defaults.
For example: In the existing
values-current.yaml, if thepersistentStorage.storageClassNameparameter is set with the valueportworx-sc, then you must set the sameportworx-scvalue in the newvalues-px-central-<pxb-release-version>. yaml. -
(Optional) Execute this step only if you have configured Prometheus and Grafana following the steps mentioned in this topic Configure Prometheus and Grafana. Delete the Prometheus operator deployment upgrade to avoid conflicts:
kubectl delete deploy prometheus-operator -n <pxb-namespace>Where
<pxb-namespace>is the namespace in which you are planning to deploy PXB. -
Delete the post install hook job:
kubectl delete job pxcentral-post-install-hook --namespace <pxb-namespace>Where
<pxb-namespace>is the namespace in which you are planning to deploy PXB.noteIf you have enabled health check, deletion of post install hook job is automatically taken care. If no, you need to delete manually with the above command.
-
Now copy and execute the command under Install using the values-px-central.yaml file in your terminal to complete the upgrade:
helm upgrade px-central portworx/px-central --namespace central --create-namespace --version 2.10.0 -f values-px-central.yamlDuring an upgrade, several components are involved, which can considerably extend the upgrade duration. Therefore, the default timeout of 5 minutes is typically inadequate, and it is necessary to increase the timeout to 120 minutes. Also ensure that, you update the helm command timeout parameter to
120mwithout fail as shown in the following command:helm upgrade px-central portworx/px-central --namespace <pxb-namespace> --version <pxb-release-version> -f px-central-values-<pxb-release-version>.yaml --timeout=120mWhere
<pxb-release-version>is the PXB version you want to upgrade to. -
Click Finish after you complete the upgrade installation.
This activates the trial version of Portworx Backup. To upgrade to the enterprise version, apply a Portworx Backup license.
You can find more information about the Portworx Backup Helm chart in the helm section.
noteIf you are on Portworx Backup version 2.0.0 and want to upgrade to version 2.0.1 or 2.0.1 or 2.1.x or 2.2.x, then set the administrator password in the
helm upgradecommand as shown below:helm upgrade px-central portworx/px-central --namespace <pxb-namespace> --version <pxb-release-version> --set oidc.centralOIDC.defaultPassword=<current-admin-password> -f values.yamlWhere
<pxb-namespace>is the namespace in which you are planning to deploy PXB and<pxb-release-version>is the PXB version you want to upgrade to.