Service Account
Service account is a specialized type of identity account used by services, applications, and automated processes to interact with PDS APIs in a secure and controlled manner.
Advantages of Service account
Service account are used in applications and systems to access resources and perform tasks. Here's how to use service accounts:
- Authenticate: Service accounts authenticate themselves using API keys, tokens, or other credentials.
- Authorization: Service accounts are authorized to access specific resources or perform certain actions based on defined permissions.
- Interactions: Service accounts interact with other services or APIs to perform tasks, retrieve data, or update resources.
- Secure communication: Service account uses JSON Web Token (JWT) tokens along with Transport Layer Security (TLS) to communicate with other services.
Service accounts are important for establishing robust safeguards for service and API key access in the following ways:
Enhanced security
- Reduced attack surface: When services use dedicated service accounts, it reduces the attack surface compared to sharing a common user account. Breaching a single service account does not automatically grant access to other systems, as each account has its own set of permissions.
- Credential management: Service accounts use secure credentials, such as API keys, tokens, or certificates, which are typically stored and managed securely. This reduces the risk of credentials being exposed and used maliciously.
Audit and monitoring
Service accounts make it easier to audit and monitor activities. Each service account's actions are logged separately, providing detailed visibility into who or what is performing which operations. This is crucial for compliance and security monitoring.
Simplified revocation and rotation
- Revocation: When a service or application no longer requires access to specific resources, its service account can be easily revoked, rendering the associated credentials useless. This is more efficient and secure than having to change the credentials of a shared user account.
- Rotation: Service account credentials can be regularly rotated for security reasons. Automated processes make it easier to update and manage these credentials in an organized manner.
API access control
Service accounts often come with access controls that allow organizations to specify which APIs or endpoints they can access. This ensures that the service account can interact only with the necessary parts of a system.
To proceed with the creation of a service account, you must have the account-admin role. Ensure that your user role meets this requirement before starting the below procedure. For more information about the account-admin role, refer to the Account Admin section.
1. Log in to obtain an authentication token
Before creating a service account (Step 2), you need to log in to the PDS platform to authenticate yourself and establish the necessary credentials to perform API operations securely. The login process, using the Login API, generates an authentication token (idToken) that is required to authorize API requests for subsequent steps.
API endpoint for login
Use the following API endpoint to log in and retrieve the idToken:
https://cloud.portworx.io/core/v1/oauth:login
Login API call
curl --location 'https://cloud.portworx.io/core/v1/oauth:login' \
--header 'Content-Type: application/json' \
--data-raw '{
"email": "<insert email ID here>",
"password": "<insert password here>"
}' | jq -r ".idToken"
where:
email: Enter the email address associated with your PDS account.password: Enter the password for the specified email address.
Example response
If the login is successful, the API returns a JSON response containing the idToken. For example:
{
"idToken": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9..."
}
The idToken is a JWT that authenticates the user and authorizes API calls.
Usage of idToken
The idToken is required as a bearer token in the Authorization header for all subsequent API requests.
For example:
--header "Authorization: Bearer <idToken>"
2. Create a service account
To create a service account:
Use the Service account API to create a service account. A service account represents an application or service that requires controlled access to PDS resources, enabling programmatic interactions with the PDS platform.
API endpoint
Use the following endpoint to create a service-account for a specific tenant (organization) resource:
https://cloud.portworx.io/core/v1/tenants/<insert-tenant-id>/serviceAccounts
Replace <insert-tenant-id> with the unique ID of the tenant (organization) for which you want to create the service account. For more information about how to retrieve the tenant (organization) ID using the Tenant Search API and from the Organization manager page in the PDS user interface, refer to the Retrieve the organization ID section.
API call
This API call creates a service account and provides the necessary credentials (clientId and clientSecret) to enable secure and controlled access to PDS resources, making it essential for integrating external applications or services with the PDS platform.
The request body is a JSON object containing details about the service account you want to create:
curl --http2 --location "https://cloud.portworx.io/core/v1/tenants/<insert-tenant-id>/serviceAccounts" \
--header 'Content-Type: application/json' \
--header 'Accept: application/json' \
--header "px-account-id: <insert-account-id>" \
--data '{
"meta": {
"name": "<insert-service-account-name>"
},
"config": {
}
}'
where: Headers:
Content-Type: application/json: Indicates that the request body is in JSON format.Accept: application/json: Requests the response in JSON format.px-account-id: The unique identifier for the account associated with the PDS setup.
Endpoints:
- The endpoint targets the
serviceAccountsresource under the specified tenant (organization). - Replace
<insert-tenant-id>with the tenant (organization) ID.
Request body:
{
"meta": {
"name": "<insert-service-account-name>"
},
"config": {
}
}
where:
meta.name: Specifies the name of the service account. Replace<insert-service-account-name>with the desired name for the service account.config: Reserved for future use; currently left empty.
Example response:
{
"meta": {
"uid": "sa:f852xxxx-xxxx-xxxx-xxxx-xxxxxx792a14",
"name": "migration-sa",
"description": "",
"resourceVersion": "1",
"createTime": "2024-05-12T07:44:08.610558Z",
"updateTime": "2024-05-12T07:44:08.610558Z",
"labels": {
"px-managed/created_by": "<creator_email>",
"px-managed/internal": "false"
},
"annotations": {},
"parentReference": {
"type": "tenants",
"version": "v1",
"uid": "ten:acc:d3755xxx-xxxx-xxxx-xxxx-xxxxx56fcb15"
},
"resourceNames": {}
},
"config": {
"clientId": "c/p4aG2xxxxxxxxxxxxxxeoTr/b05",
"clientSecret": "e9870bxxxxxxxxafe9ab43bc",
"disabled": false
},
"status": {
"secretGenerationCount": 1,
"lastSecretUpdateTime": "2024-05-12T07:44:08.609170363Z"
}
}
where in config:
clientId: The unique identifier for the service account.clientSecret: The secret associated with the service account, used for generating access tokens.disabled: Indicates whether the service account is active (false) or disabled (true).
Example workflow
-
Replace placeholders with actual values:
- Tenant (organization) ID: Replace
<insert-tenant-id>with the tenant (organization) ID. - Account ID: Replace
<insert-account-id>with the account ID. - Token: Replace
<insert-token>with the idToken obtained during login. - Service Account Name: Replace
<insert-service-account-name>with the desired name.
- Tenant (organization) ID: Replace
-
Execute the command using
curl. -
Copy the
meta.uid,config.clientIdandconfig.clientSecretfrom the response. These values will be used in subsequent steps, such as creating IAM and generating access tokens for authenticating the service account.
3. Associate a service account with a role
After creating the service account, the next step is to associate the service account with a specific role using the IAM API. This step ensures the service account has the necessary permissions to access resources and APIs as defined by the assigned role.
- A service account can have a role of up to organization admin (also referred to as
tenant-admin). This is the highest role that can be assigned to a service account. For more information about the organization admin role, refer to the Organization Admin section.
-
Define the IAM configuration:
- Specify the
actorIdas the service account ID created in the above procedure. - Set the
actorTypetoSERVICE_ACCOUNTto identify the type of actor. - Define the
accessPolicyto associate the service account with a role (for example,tenant-admin) and the required resource IDs.
- Specify the
-
Send an HTTP request to the following endpoint to create the IAM configuration:
https://cloud.portworx.io/core/v1/iamExample IAM API request:
curl --http2 --location 'https://cloud.portworx.io/core/v1/iam' \
--header 'Content-Type: application/json' \
--header 'Accept: application/json' \
--header "px-account-id: "<insert account id here. Ex: acc:xxxxxxxx-xxxx-xxxx-xxxx-57602280771a >" \
--data '{
"meta": {
"name": "sa-iam"
},
"config": {
"actorId": "<insert service account id here. Ex: sa:xxxxxxxx-xxxx-xxxx-xxxx-a783d919d356 >",
"actorType": "SERVICE_ACCOUNT",
"accessPolicy": {
"tenant": [
{
"roleName": "tenant-admin",
"resourceIds": [
"<insert tenant id here. Ex: ten:acc:xxxxxxxx-xxxx-xxxx-xxxx-57602280771a >"
]
}
]
}
}
}'where:
actorId: The unique ID of the service account created in Step 1.actorType: Set toSERVICE_ACCOUNTto indicate that the actor is a service account.accessPolicy: Defines the role and the resources the service account can access.roleName: Specifies the role to be assigned (for example,tenant-admin).resourceIds: The IDs of the resources the service account can access.
noteThe token used in the
Authorizationheader for this API request is theidTokenobtained during the login step (Step 1). To retrieve this token, use the/core/v1/oauthendpoint. This token is required to authenticate and authorize the request. To authenticate this request:-
Obtain the idToken by logging in using the
/core/v1/oauthendpoint. -
Replace
<insert idToken obtained from /core/v1/oauth:login here>in theAuthorizationheader with the token retrieved from Step 1.
This ensures the API call is authorized properly.
Example response
{
"meta": {
"uid": "iam:abc12345-6789-xyz",
"name": "sa-iam",
"createTime": "2024-11-18T12:34:56.789Z"
},
"status": {
"reason": "IAM created successfully",
"phase": "ACTIVE"
}
}
This step associates the service account with a role (for example, tenant-admin) and grants it access to resources as per the assigned role's permissions. This is essential for enabling the service account to authenticate and interact with PDS APIs effectively.
Proceed to the next step to generate an access token for the service account.
4. Generate access token from service account
This API call is essential for enabling service accounts to interact with the PDS platform securely. The generated JWT token:
- Authenticates API requests: Validates the service account's identity.
- Grants access: Provides controlled access to resources and operations based on the service account's assigned role and permissions.
- Ensures security: Uses client-specific credentials (
clientIdandclientSecret) to maintain secure and isolated access.
For more information about the API, view the documentation.
Use the following endpoint to generate a JWT for a service account:
https://cloud.portworx.io/core/v1/tenants/<insert tenant id here>:getToken
Replace <insert-tenant-id> with the unique identifier of the tenant (organization) associated with the service account.
This is the URL endpoint where you will send an HTTP/2 request to generate a JWT token for a service account. The endpoint is specifically designed for creating tokens, and it does not require a dynamic identifier (for example, user or account ID) in the URL.
API call
The request body is a JSON object that contains the details necessary to generate the JWT token:
curl --http2 --location 'https://cloud.portworx.io/core/v1/tenants/<insert tenant id here>:getToken' \
--header 'Content-Type: application/json' \
--header 'Accept: application/json' \
--header "px-account-id: <insert-account-id>" \
--data '{
"clientId": "<insert-client-id>",
"clientSecret": "<insert-client-secret>"
"expiry": "<insert-custom-expiration-time>"
}' | jq -r ".token"
If a custom expiry time is not specified, the token will have a default time-to-live (TTL) of 60 minutes, after which it will expire. To continue, you must generate a new token by following the steps outlined in the next section.
Request body
{
"clientId": "<insert-client-id>",
"clientSecret": "<insert-client-secret>",
"expiry": "<insert-custom-expiration-time>"
}
where:
clientId: The unique identifier for the service account, obtained when the service account was created.clientSecret: The secret key associated with the service account, also provided during the service account creation.expiry: custom expiry time for the client secret- The
| jq -r ".token"filters the response to extract and display only the JWT token.
Example workflow
-
Replace the placeholders with actual values:
- Tenant (organization) ID: Replace
<insert-tenant-id>with the tenant (organization) ID. - Account ID: Replace
<insert-account-id>with the account ID. - Client ID and Secret: Replace
<insert-client-id>and<insert-client-secret>with the credentials generated during the service account creation step.
- Tenant (organization) ID: Replace
-
Run the command using
curl.The response will return a JWT token.
Example response
{
"token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9..."
}
-
token: The JWT token generated for the service account. This token is used for authenticating API requests made by the service account.noteThe token provided has a limited time-to-live (TTL) of 60 minutes, after which it will expire. You should generate a new token following the instructions detailed in the next section.
5. Use the generated token in subsequent API calls
After generating a JWT token for the service account in Step 4, you can use this token to authenticate and authorize subsequent API requests made by the service account. The token, included in the Authorization header, ensures secure access to PDS resources and APIs.
For every API request made by the service account, include the Authorization header in the HTTP request with the following format:
--header "Authorization: Bearer <insert-generated-token>"
where:
Authorization: Specifies the authentication mechanism.Bearer: Indicates that the header contains a token used for access control.<insert-generated-token>: Replace this placeholder with the JWT token obtained in Step 4.
Example Usage in an API Call
Here’s how to include the token when calling another API, such as fetching details about a tenant (organization):
curl --http2 --location 'https://cloud.portworx.io/core/v1/tenants/<tenant-id>' \
--header 'Content-Type: application/json' \
--header 'Accept: application/json' \
--header "Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIs..."
Retrieve the Organization ID
You can retrieve the organization-id in Portworx through one of the following methods:
- From the organization manager in the PDS user interface.
- Using the Tenant Search API.
From the organization manager in the PDS user interface
To locate the organization ID using the PDS user interface:
-
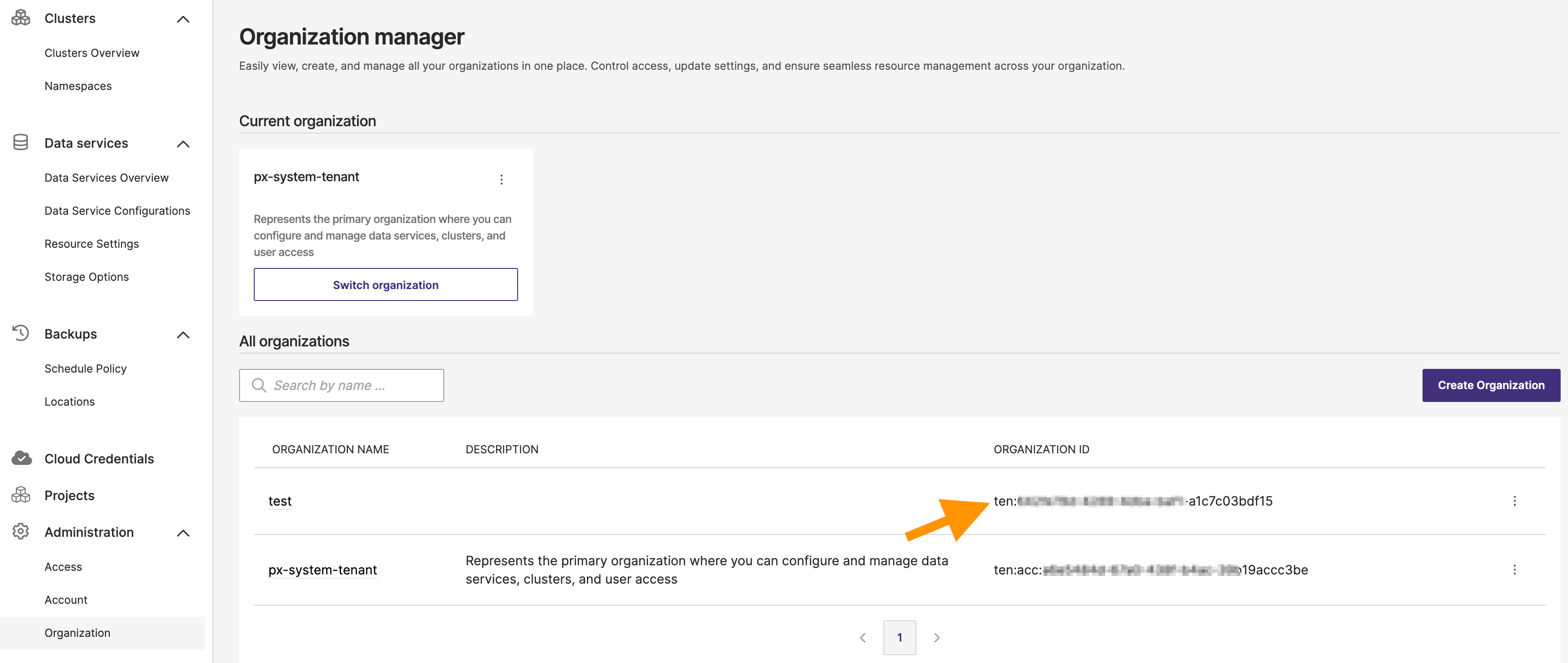
Navigate to Administration in the main menu and select Organization from the dropdown.
-
On the Organization manager page -> All organizations section, The organization ID for each organization is listed in the corresponding row under the Organization ID column.
Using the Tenant Search API
This API retrieves information on all available organizations, where each organization’s unique identifier (UID) is found in the response as the uid field. Follow the steps below to retrieve the organization ID.
To retrieve organization (tenant) information:
-
Send a GET request to the Tenant Search API endpoint:
GET https://portworx.github.io/core/v1/tenants:searchnoteThis API call requires an authentication token for successful execution. Include the token in the Authorization header as follows:
curl --location --request GET 'https://portworx.github.io/core/v1/tenants:search' \
--header "Authorization: Bearer <insert-token-here>" \
--header 'Accept: application/json'Replace
<insert-token-here>with theidTokenobtained from the login step using the/core/v1/oauth:loginendpoint. This token authenticates the request and ensures access to tenant data. -
Interpret the response.
The API response contains an array of organization objects under the tenants field. Each organization has a
metasection with various fields.Example response:
{
"tenants": [
{
"meta": {
"uid": "ten:0283xxx-xxx-xxx-xxxx-xxxxxx",
"name": "tenant-1",
"description": "test",
"resourceVersion": "2",
"createTime": "2024-10-24T09:08:35.746949Z",
"updateTime": "2024-11-05T08:15:50.749629Z",
"labels": {
"px-managed/created_by": "pds-account-admin@purestorage.com"
},
"annotations": {},
"parentReference": {
"type": "accounts",
"version": "v1",
"uid": "acc:eeexxxxxxxxx"
},
"resourceNames": {
"acc:eee8a69xxxxxxx": "dev"
}
},
"status": {
"reason": "Update completed, initiated by pds-account-admin@purestorage.com",
"phase": "ACTIVE"
}
}
],
"pagination": {
"totalRecords": "2",
"currentPage": "1",
"pageSize": "10",
"totalPages": "1",
"nextPage": "-1",
"prevPage": "-1"
}
}
This process allows PDS users to programmatically access the unique organization ID required for organization-specific configurations.
Best practices
When working with service accounts, consider these best practices:
- Follow the principle of least privilege: Grant the minimum permissions necessary for the service to perform its tasks.
- Securely store and manage service account credentials to prevent unauthorized access.
- Implement logging and auditing to track service account activities for security and compliance.
- Use secure communication protocols like HTTPS to protect credentials and data in transit.
- Regularly review and update permissions to ensure they remain aligned with the service's requirements.
- Rotate service account credentials periodically for improved security.
- Educate your team on security best practices and the use of service accounts.
Service accounts play a critical role in modern application development and security, enabling secure, automated, and controlled interactions between services and components. Understanding and implementing best practices is essential for maintaining a robust and secure system.
User account versus user API keys versus service account
- User account: User accounts represent individual users and their access permissions. They are associated with human-readable usernames, passwords, and sometimes additional information such as email addresses and roles.
- User API keys: These are typically associated with user accounts and grant access based on the user's permissions. User API keys are used for user-specific tasks and are tied to a specific user account.
- Service account: Service accounts represent applications, services, or components. They are used for programmatic access to resources and are typically associated with API keys or tokens. Service accounts lack the human-specific attributes of user accounts and are designed for machine-to-machine communication.