Configure Backend REST API
A backend REST API refers to the interface that connects the front-end or user-facing applications with the backend servers, databases, or services. The backend REST API is responsible for handling the core logic of the system, database interactions, and any background services.
With Portworx Backup backend rest API you can perform the following tasks:
- Create roles
- Update roles
- List roles
- Delete roles
- Map roles
- Unmap roles
To configure backend rest API, you need to fetch an access token for the instance.
Fetch authorization bearer token
To fetch the token for an instance, login with the admin credentials and then perform the following steps:
-
Access Portworx Backup web console and login with administrator credentials:
-
In the home page, from the left navigation pane, click User Profile icon and choose PX-Backup Security.
-
Right-click on the PX-Backup Security page and select Inspect from the context menu. This opens the browser's developer tools.
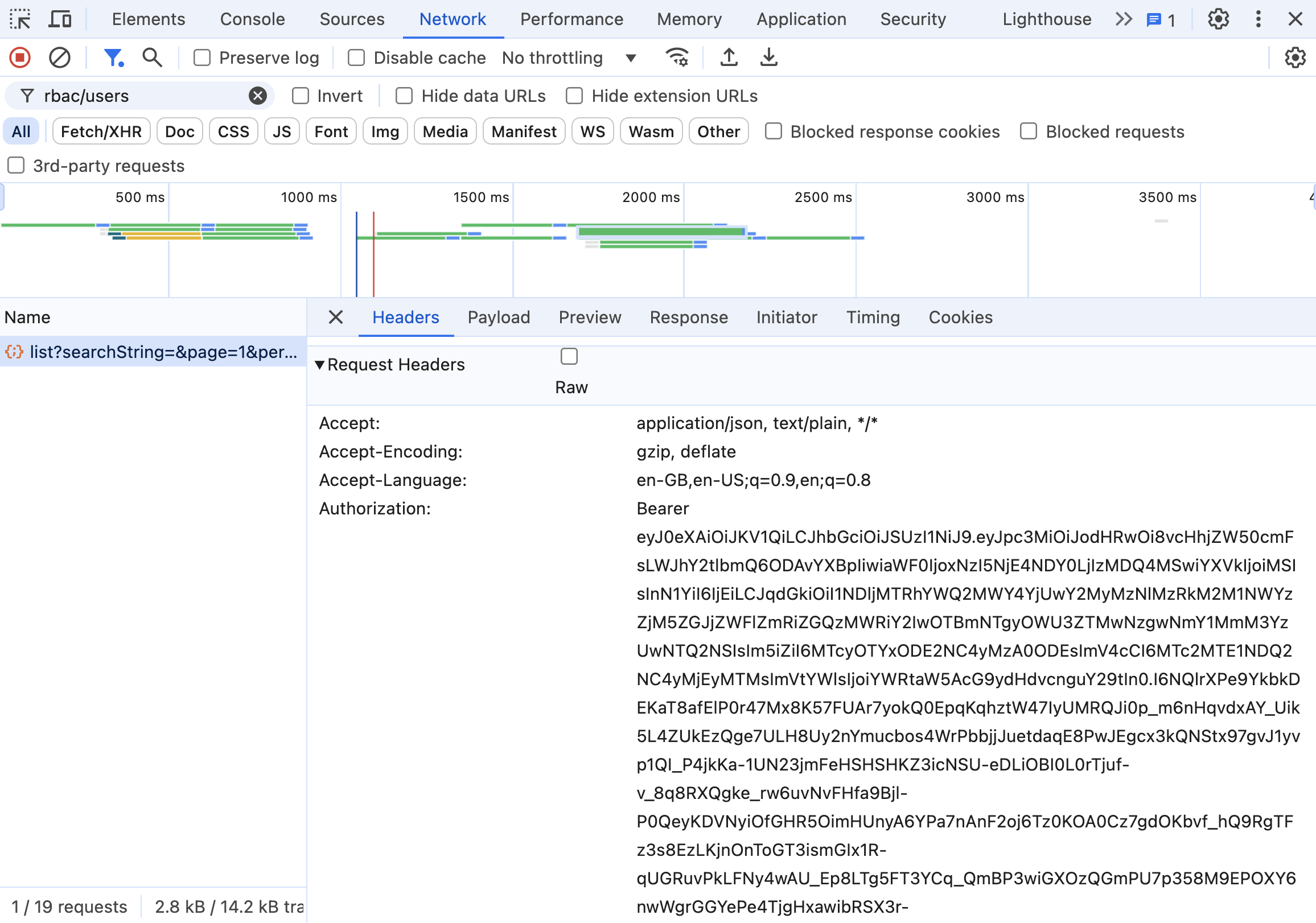
-
In the developer tools page, navigate to Networks tab and wait for the below endpoint to load in Name column. You can also search with rbac/users in the filter tab and search for this endpoint.
http://<end-point>/Backend/api/pxBackup/rbac/users/list?searchString=&page=1&per_page=10Name column typically shows the requests being made, which includes specific APIs being called or resources being fetched during a web application's operation.
-
Select the above API endpoint from the Name column and move to Request Headers row and copy the bearer token from Authorization section. Make sure you copy only the token and not the Bearer string that appears before the token.
-
Export the token with the following command:
export TOKEN="BEARER <token-copied-from-authorization-field>" -
Run the below API calls to check if the token functions, make sure you replace the endpoint with the actual server address:
% curl -k -X GET "http://<end-point>/backend/api/pxBackup/rbac/roles/list" -H "accept: application/json" -H "Authorization: $TOKEN"Sample output:
{"SUCCESS":true,"DATA":{"current_page":1,"searched":false,"first_page_url":"","from":0,"last_page":1,"last_page_url":"","next_page_url":"","path":"","per_page":10,"to":5,"total":5,"metaData":null,"data":[{"metadata":{"name":"px-backup-super.admin","uid":"<alpha-numeric-uid>","org_id":"default","create_time":{"seconds":1729158677,"nanos":332422260},"last_update_time":{"seconds":1729158743,"nanos":476343054},"create_time_in_sec":1729158677,"ownership":{"owner":"<owner-uid>","public":{"type":1}},"description":"Has full control to create, view, edit, and delete clusters, namespaces, cloud accounts, backup locations, schedule policies, rules, backups, restores, roles, users, and user groups, either created by themselves or by other users."},"rules":[{"services":["schedulepolicy","cloudcredential","backuplocation","rules","role","receiver","recipient","audit"],"apis":["*"]}],"role_id":"<alpha-numeric-role-id>"},{"metadata":{"name":"px-backup-infra.admin","uid":"<alpha-numeric-uid>","org_id":"default","create_time":{"seconds":1729158677,"nanos":370751364},"last_update_time":{"seconds":1729158743,"nanos":243144225},"create_time_in_sec":1729158677,"ownership":{"owner":"<owner-uid>","public":{"type":1}},"description":"Can create, view, edit, and delete cloud accounts, backup locations, schedule policies, rules, roles, users, and user groups they have created. In addition, they can view shared backup resources."},"rules":[{"services":["schedulepolicy","cloudcredential","backuplocation","rules","role","receiver","recipient"],"apis":["*"]},{"services":["audit"],"apis":["inspect*","enumerate*"]}],"role_id":"<alpha-numeric-role-id>"},{"metadata":{"name":"px-backup-app.admin","uid":"<alpha-numeric-uid>","org_id":"default","create_time":{"seconds":1729158677,"nanos":378614407},"last_update_time":{"seconds":1729158743,"nanos":351234891},"create_time_in_sec":1729158677,"ownership":{"owner":"<owner-uid>,"public":{"type":1}},"description":"Can create, edit, view, and delete backup locations, schedule policies, and rules they have created. They can also view all other shared backup resources."},"rules":[{"services":["schedulepolicy","backuplocation","rules"],"apis":["*"]},{"services":["role"],"apis":["inspect*","enumerate*","validate*"]},{"services":["cloudcredential"],"apis":["inspect*","enumerate*"]},{"services":["recipient"],"apis":["*"]},{"services":["receiver"],"apis":["enumerate*"]}],"role_id":"<alpha-numeric-role-id>"},{"metadata":{"name":"px-backup-app.user","uid":"<alpha-numeric-uid>","org_id":"default","create_time":{"seconds":1729158677,"nanos":386510867},"last_update_time":{"seconds":1729158743,"nanos":413840572},"create_time_in_sec":1729158677,"ownership":{"owner":"<owner-uid>","public":{"type":1}},"description":"Can only view the shared resources created by other roles."},"rules":[{"services":["schedulepolicy","cloudcredential","backuplocation","rules","role"],"apis":["inspect*","enumerate*","validate*"]},{"services":["recipient"],"apis":["*"]},{"services":["receiver"],"apis":["enumerate*"]}],"role_id":"<alpha-numeric-role-id>"},{"metadata":{"name":"test-role","uid":"<alpha-numeric-uid>","org_id":"default","create_time":{"seconds":1729227011,"nanos":248356472},"last_update_time":{"seconds":1729227011,"nanos":248356472},"create_time_in_sec":1729227011,"ownership":{"owner":"<owner>","public":{"type":1}},"description":"NA"},"rules":[{"services":["cloudcredential"],"apis":["inspect*","enumerate*"]},{"services":["schedulepolicy"],"apis":["inspect*","enumerate*"]},{"services":["backuplocation"],"apis":["inspect*","enumerate*"]},{"services":["rules"],"apis":["inspect*","enumerate*"]},{"services":["role"],"apis":["inspect*","enumerate*"]}],"role_id":"<alpha-numeric-role-id>"}],"fromCache":false,"networkTimer":null,"processTimer":null,"dsRequestId":0,"next_token":""},"SUCCESSMESSAGE":"Fetched all roles"}