Install Portworx on Red Hat OpenShift Service on AWS
Follow the instructions on this page to install Portworx on Red Hat OpenShift Services on AWS with console plugin.
Prerequisites
- You must have a Red Hat OpenShift Service on AWS (ROSA) cluster with bring-your-own-VPC (BYO-VPC) configuration deployed on infrastructure that meets the minimum requirements for Portworx.
- Your cluster must be running OpenShift 4.12 or higher
- Your instance size must be at least m5.xlarge with 3 compute nodes and have 3 availability zones
- Your cluster must meet AWS prerequisites for ROSA
- Ensure that OCP service is enabled from your AWS console
- AWS CLI installed and configured
- ROSA CLI installed and configured
- Ensure that any underlying nodes used for Portworx in OCP have Secure Boot disabled
Create a Portworx user
Before installing Portworx, you must create an AWS user with the required permissions.
-
From the IAM page, click Users in the left pane.
-
On the Users page, click Create user in the upper-right corner of the screen to create a new user.
-
Specify your user details and click Next.
-
On the Set permissions window, select Attach policies directly and click Create policy.
-
Copy and paste the following into the JSON tab of the policy editor and click Next:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"ec2:AttachVolume",
"ec2:ModifyVolume",
"ec2:DetachVolume",
"ec2:CreateTags",
"ec2:CreateVolume",
"ec2:DeleteTags",
"ec2:DeleteVolume",
"ec2:DescribeTags",
"ec2:DescribeVolumeAttribute",
"ec2:DescribeVolumesModifications",
"ec2:DescribeVolumeStatus",
"ec2:DescribeVolumes",
"ec2:DescribeInstances",
"autoscaling:DescribeAutoScalingGroups"
],
"Resource": [
"*"
]
}
]
} -
Provide a name for your policy and click Create policy. Once your policy is successfully created and attached to your user account, it will be listed in the Permissions policies section.
-
Select your policy in the Permissions policies section and click Next.
-
Review your user details and permissions, and Create user.
Create AWS secure credentials
Once the policy is created in the previous section, you need to create credentials for securely logging into your AWS account.
-
From the User window, search for your user account created in the previous section using the search bar.
-
Once you click your user account name, you navigate to your account information page. Click the Security credentials tab under the Summary section on the info page.
-
Select Create access key from the Access keys section.
-
Select the Application running on an AWS compute service option and click Next.
-
Provide the description tag value and click Create access key.
-
Click Download .csv file to save your credentials.
-
Use the values from the CSV file to create an AWS Secret in OpenShift:
oc create secret generic -n portworx aws-creds \
--from-literal=aws-key=XXXXXXXXXXXXXX \
--from-literal=aws-secret=XXXXXXXXXXXX
Open ports for worker nodes
Perform the following to add the inbound rules so that the AWS EC2 instance uses your specified security groups to control the incoming traffic.
-
From the EC2 page of your AWS console, click Security Groups, under Network & Security, in the left pane.
-
On the Security Groups page, type your ROSA cluster name in the search bar and press enter. You will see a list of security groups associated with your cluster. Click the link under Security group ID of your cluster's worker security group:
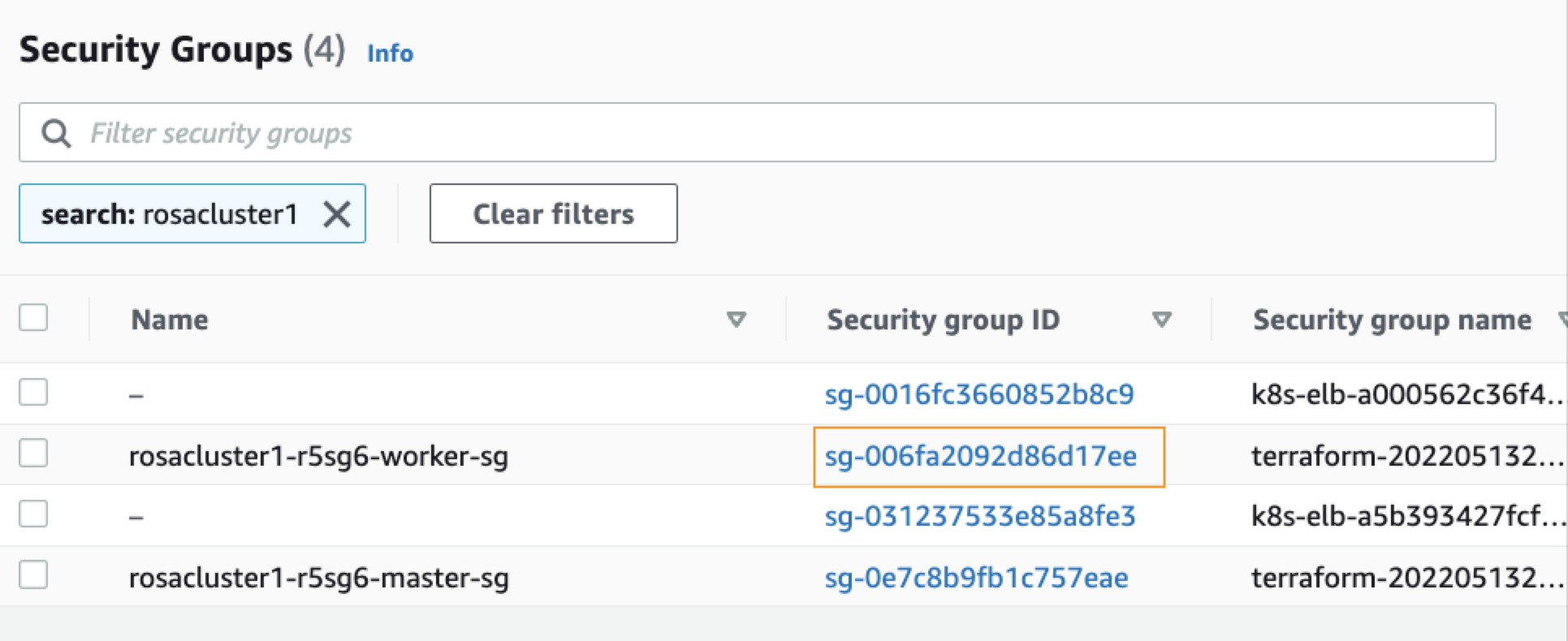
-
From your security group page, click Actions in the upper-right corner, and choose Edit inbound rules from the dropdown menu.
-
Click Add Rule at the bottom of the screen to add each of the following rules:
- Allow inbound Custom TCP traffic with Protocol: TCP on ports 17001 - 17022
- Allow inbound Custom TCP traffic with Protocol: TCP on port 20048
- Allow inbound Custom TCP traffic with Protocol: TCP on port 111
- Allow inbound Custom UDP traffic with Protocol: UDP on port 17002
- Allow inbound NFS traffic with Protocol: TCP on port 2049
Make sure to specify the security group ID of the same worker security group that is mentioned in step 2.
-
Click Save rule.
Create a monitoring ConfigMap
Newer OpenShift versions do not support the Portworx Prometheus deployment. As a result, you must enable monitoring for user-defined projects before installing the Portworx Operator. Use the instructions in this section to configure the OpenShift Prometheus deployment to monitor Portworx metrics.
To integrate OpenShift’s monitoring and alerting system with Portworx, create a cluster-monitoring-config ConfigMap in the openshift-monitoring namespace:
apiVersion: v1
kind: ConfigMap
metadata:
name: cluster-monitoring-config
namespace: openshift-monitoring
data:
config.yaml: |
enableUserWorkload: true
The enableUserWorkload parameter enables monitoring for user-defined projects in the OpenShift cluster. This creates a prometheus-operated service in the openshift-user-workload-monitoring namespace.
Install Portworx
Follow the instructions in this section to deploy Portworx.
Generate Portworx spec
-
Sign in to the Portworx Central console.
The system displays the Welcome to Portworx Central! page. -
In the Portworx Enterprise section, select Generate Cluster Spec.
The system displays the Generate Spec page. -
From the Portworx Version dropdown menu, select the Portworx version to install.
-
For Platform, choose AWS. Under Distribution Name, select Red Hat OpenShift Service on AWS (ROSA). Enter your cluster's Kubernetes version, then click Save & Download to generate the specs.
Modify the spec to use AWS Secrets
To pass the AWS secrets to Portworx, modify your generated spec to include the AWS credentials using environment variables. Update the spec with the following:
env:
- name: AWS_ACCESS_KEY_ID
valueFrom:
secretKeyRef:
key: aws-key
name: aws-creds
- name: AWS_SECRET_ACCESS_KEY
valueFrom:
secretKeyRef:
key: aws-secret
name: aws-creds
Log in to OpenShift UI
Log in to the OpenShift console by following the quick access instructions on the Accessing your cluster quickly page in the Red Hat OpenShift Service on AWS documentation.
Install Portworx Operator using the OpenShift UI
-
From your OpenShift UI, select OperatorHub in the left pane.
-
On the OperatorHub page, search for Portworx and select the Portworx Enterprise card:
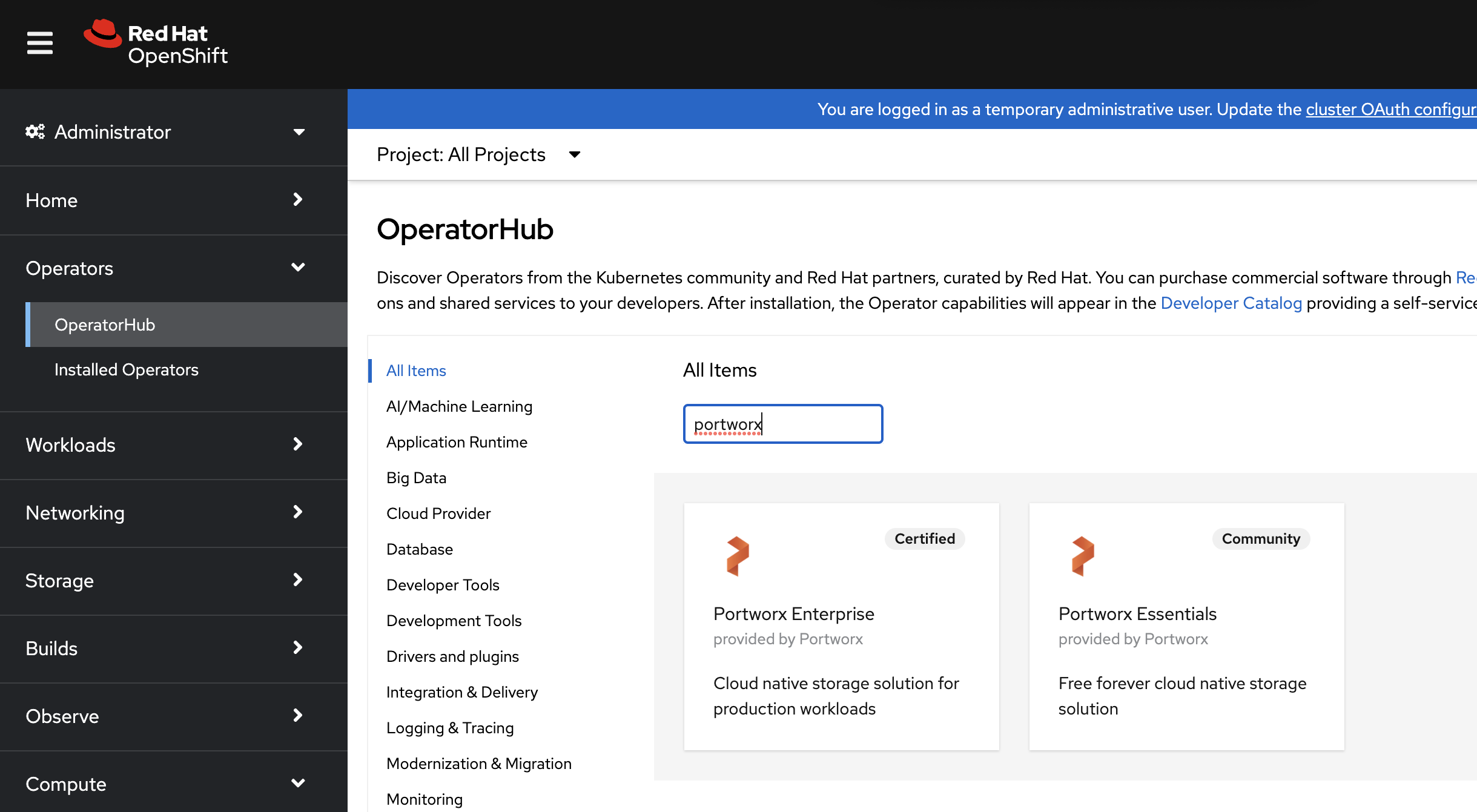
-
Click Install to install Portworx Operator:
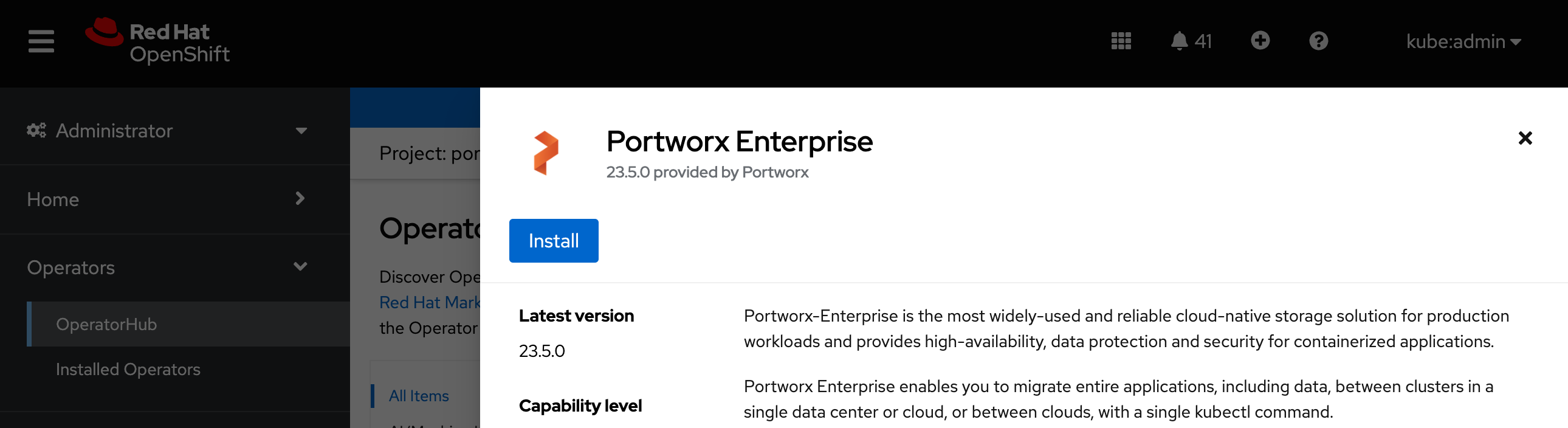
-
Portworx Operator begins to install and takes you to the Install Operator page. On this page:
- Select the A specific namespace on the cluster option for Installation mode.
- Choose the Create Project option from the Installed Namespace dropdown.
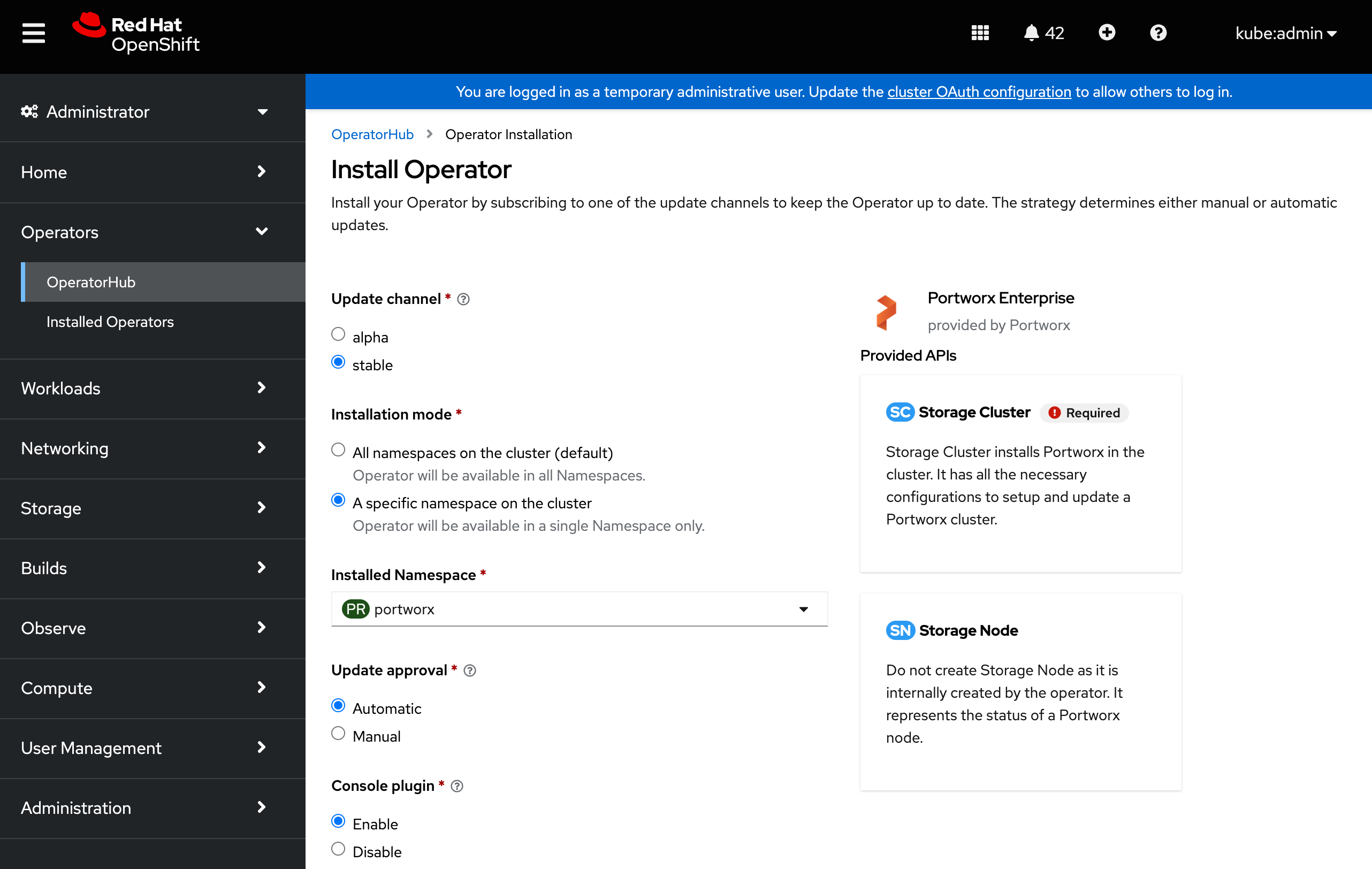
-
In the Create Project window, provide the name
portworxand click Create to create a namespace called portworx. -
To manage your Portworx cluster using the Portworx dashboard within the OpenShift UI, select Enable for the Console plugin option.
-
Click Install to deploy Portworx Operator in the
portworxnamespace.
Apply Portworx spec using OpenShift UI
-
Once the Operator is installed successfully, create a StorageCluster object from the same page by clicking Create StorageCluster:
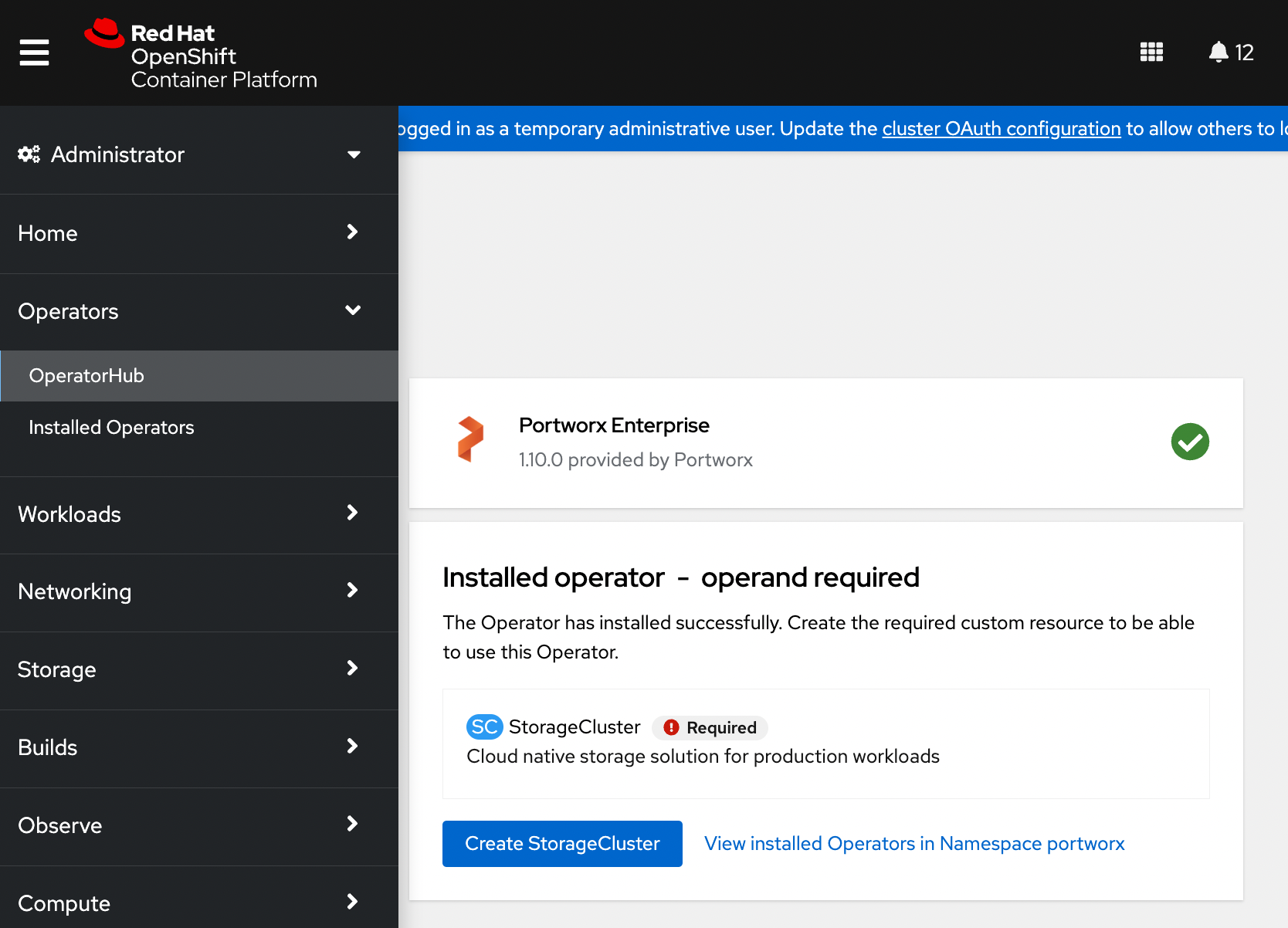
-
On the Create StorageCluster page, choose YAML view to configure a StorageCluster.
-
Copy and paste the Portworx spec you generated in the Generate Portworx spec section step into the text-editor, and click Create to deploy Portworx:
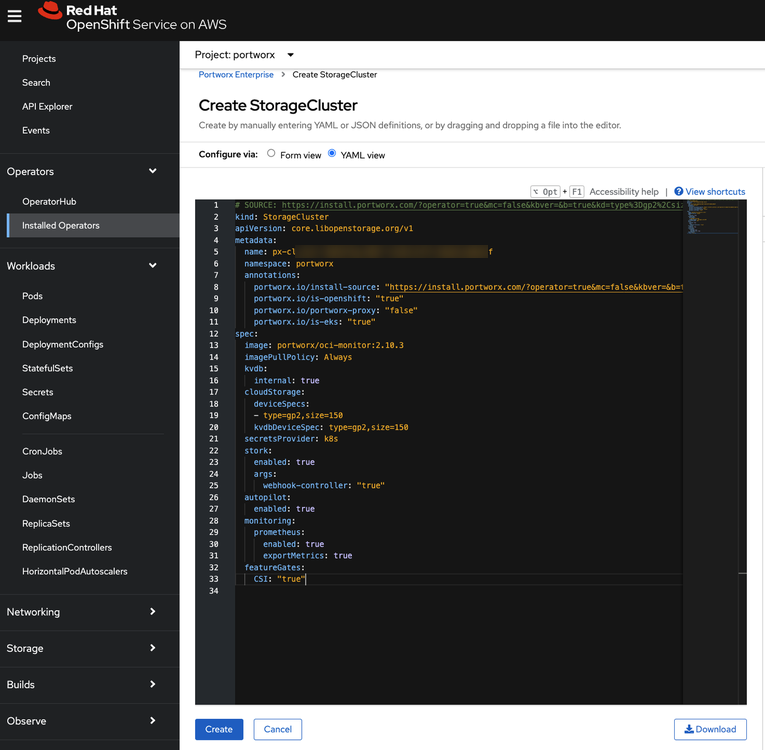
-
Verify that Portworx has deployed successfully by navigating to the Storage Cluster tab of the Installed Operators page. Once Portworx has been fully deployed, the status will show as Online:
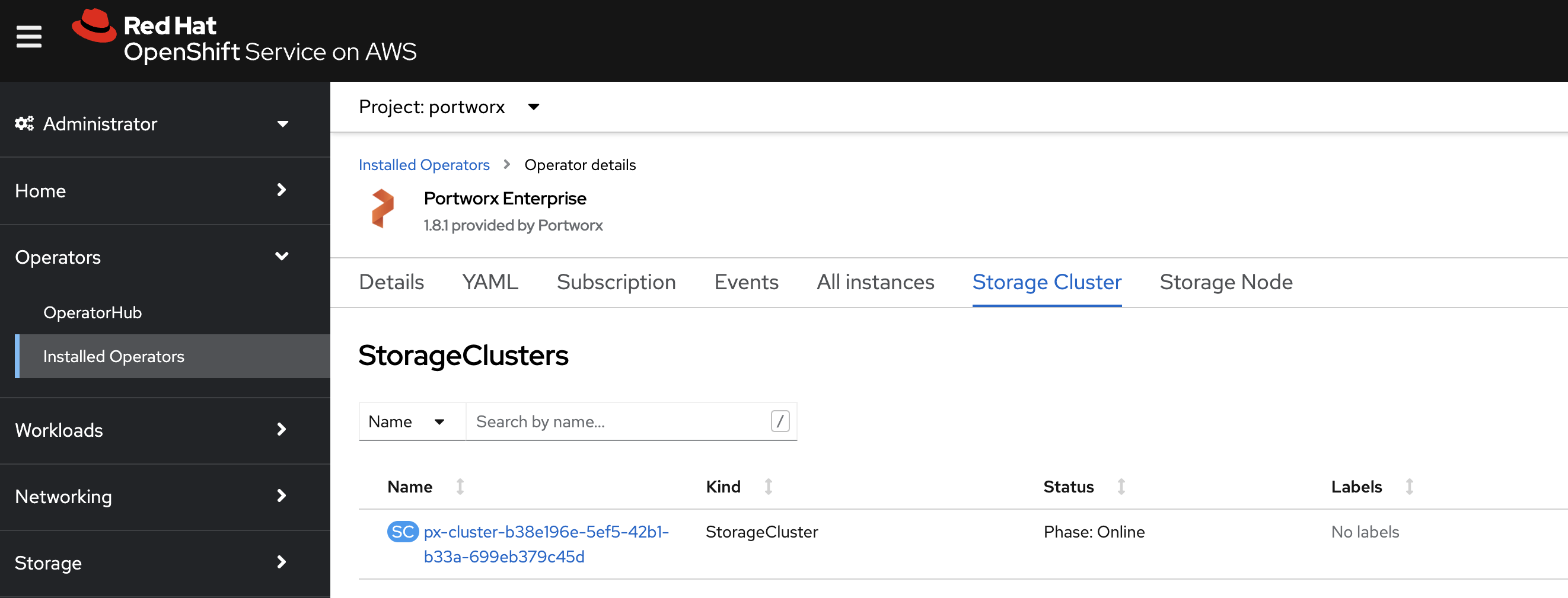
-
Refresh your browser to see the Portworx option in the left pane. Click the Cluster sub-tab to access the Portworx dashboard.
Verify your Portworx installation
Once you've installed Portworx, you can perform the following tasks to verify that Portworx has installed correctly.
Verify Portworx cluster status
-
Once you have created the StorageCluster, you can see the Portworx option in the left pane of the OpenShift UI. Click the Cluster sub-tab to view the Portworx dashboard.
-
If Portworx has been installed correctly, the status will be displayed as Running. You can also see the information about the status of Telemetry, Monitoring, and the version of Portworx and its components installed in your cluster.
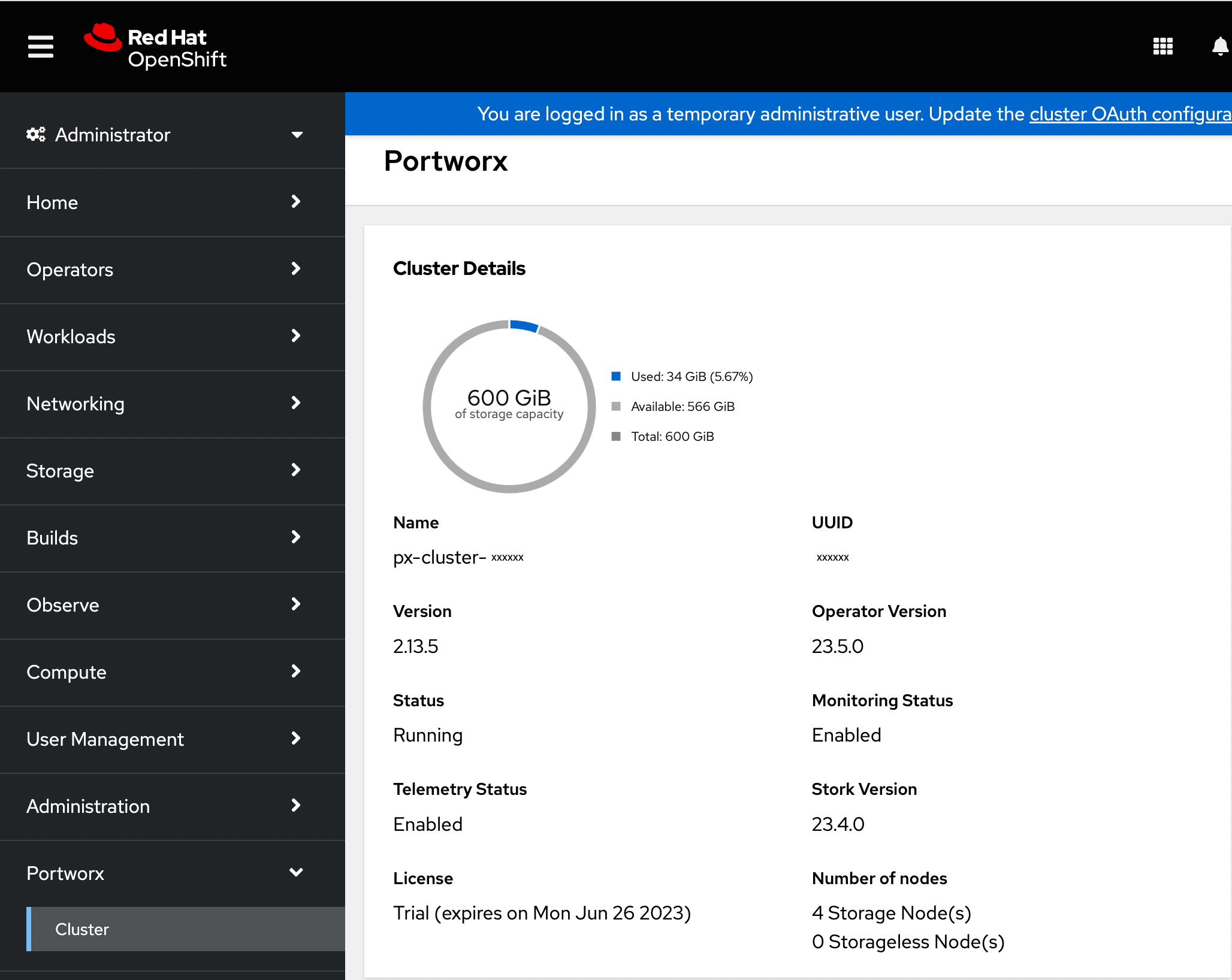
-
Navigate to the Node Summary section. If your cluster is running as intended, the status of all Portworx nodes should be Online.
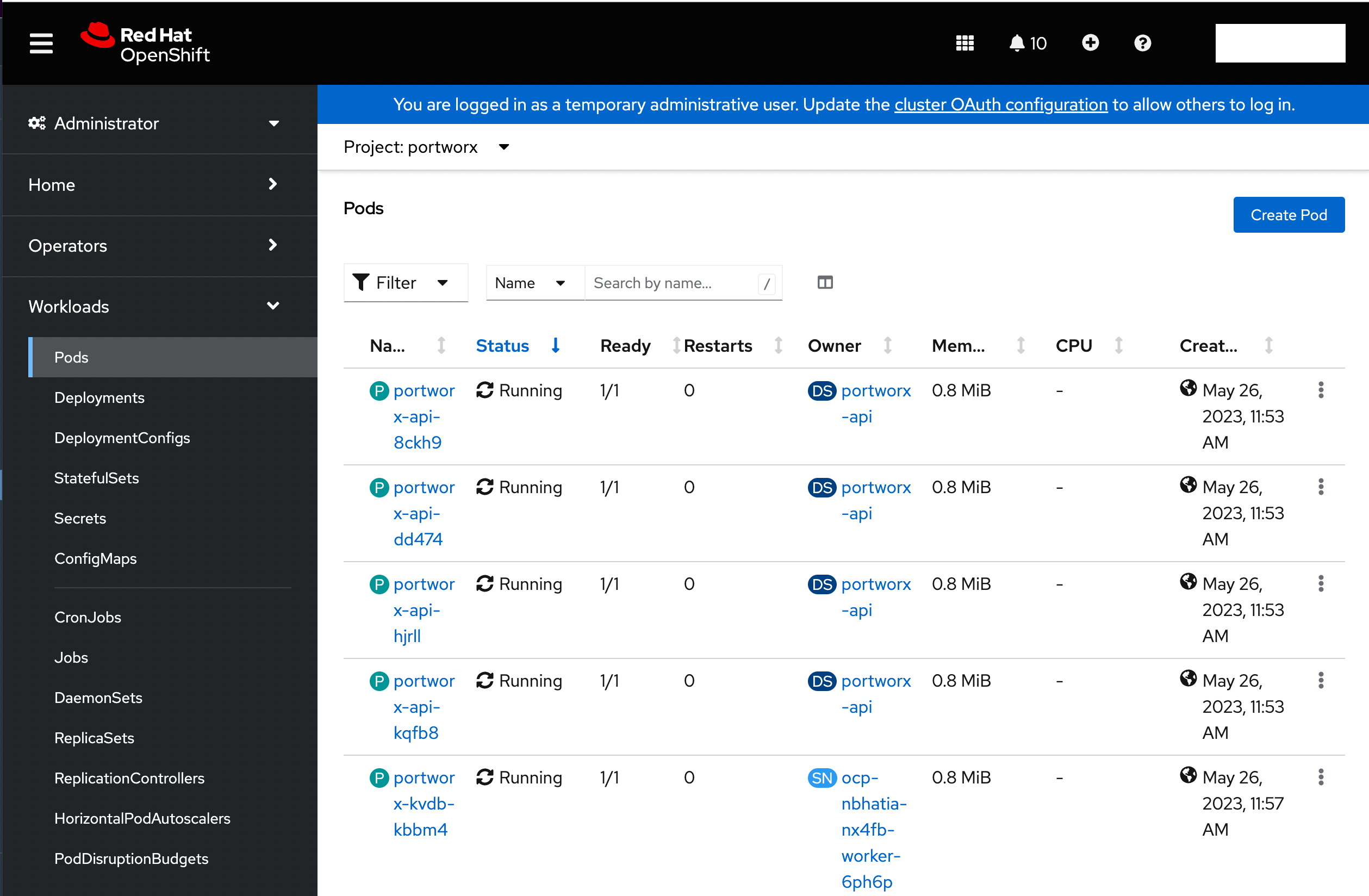
Verify if all pods are running
From the left pane of the OpenShift UI, click Pods under the Workload option. To check the status of all pods in the portworx namespace, select portworx from the Project drop-down. If Portworx is installed correctly, then all pods should be in the Running status:
Create your first PVC
For your apps to use persistent volumes powered by Portworx, you must use a StorageClass that references Portworx as the provisioner. Portworx includes a number of default StorageClasses, which you can reference with PersistentVolumeClaims (PVCs) you create. For a more general overview of how storage works within Kubernetes, refer to the Persistent Volumes section of the Kubernetes documentation.
Perform the following steps to create a PVC:
-
Paste the following in the text-editor to create a PVC referencing the
px-csi-dbdefault StorageClass and click Create:kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: px-check-pvc
spec:
storageClassName: px-csi-db
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 2Gi -
Run the
oc applycommand to create a PVC:oc apply -f <your-pvc-name>.yamlpersistentvolumeclaim/example-pvc created
Verify your StorageClass and PVC
-
Navigate to the Portworx dashboard by clicking Cluster under the Portworx option in the left pane.
-
Scroll to the Volumes section under Cluster details to view the status of your PVCs:
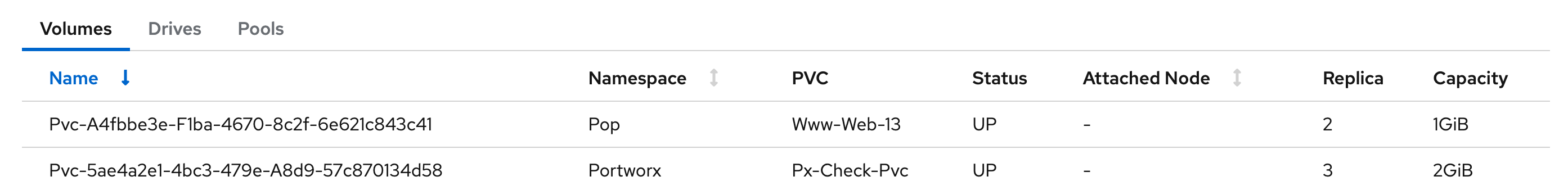
The
Upstatus indicates that the PVC is successfully bound to a Persistent Volume and is available for use.